As our homes and workplaces become increasingly connected, the Internet of Things (IoT) has transformed from a buzzword into an everyday reality. From smart thermostats to industrial sensors, these devices not only make our lives more convenient but also create new IoT security challenges. Each connected device represents a potential entry point for cybercriminals, making IoT security more critical than ever.
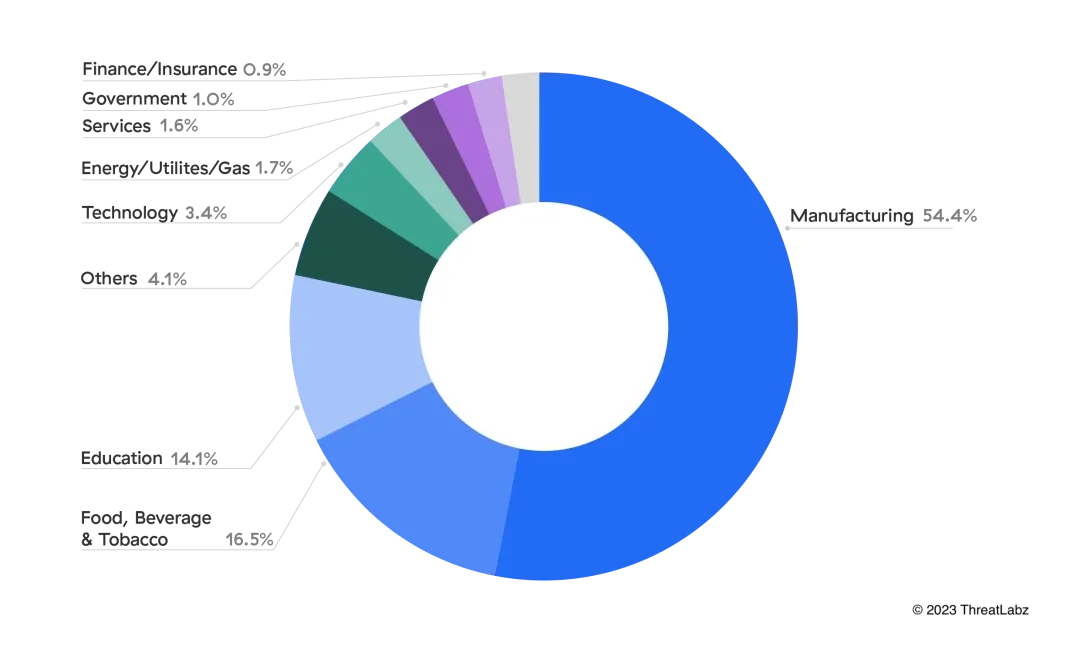
Breakdown of verticals targeted by IoT malware attacks
With cyberattacks becoming increasingly sophisticated, even a single vulnerable IoT device can compromise an entire IoT network security. In today's connected business landscape, investing in an IoT security solution is not merely an IT concern—it is a business imperative. Organizations that neglect IoT security services risk exposing sensitive data, facing operational disruptions, and damaging their reputation.
In this blog, we are diving into IoT security challenges and best practices that help businesses significantly reduce their exposure to IoT security risks and maintain healthy IoT cybersecurity.
What is IoT Security?
Internet of Things security refers to the set of technologies, protocols, and practices designed to protect connected devices, networks, and data in the IoT ecosystem from unauthorized access, cyberattacks, and vulnerabilities throughout their lifecycle. It encompasses hardware security, data encryption, network security, and identity management.
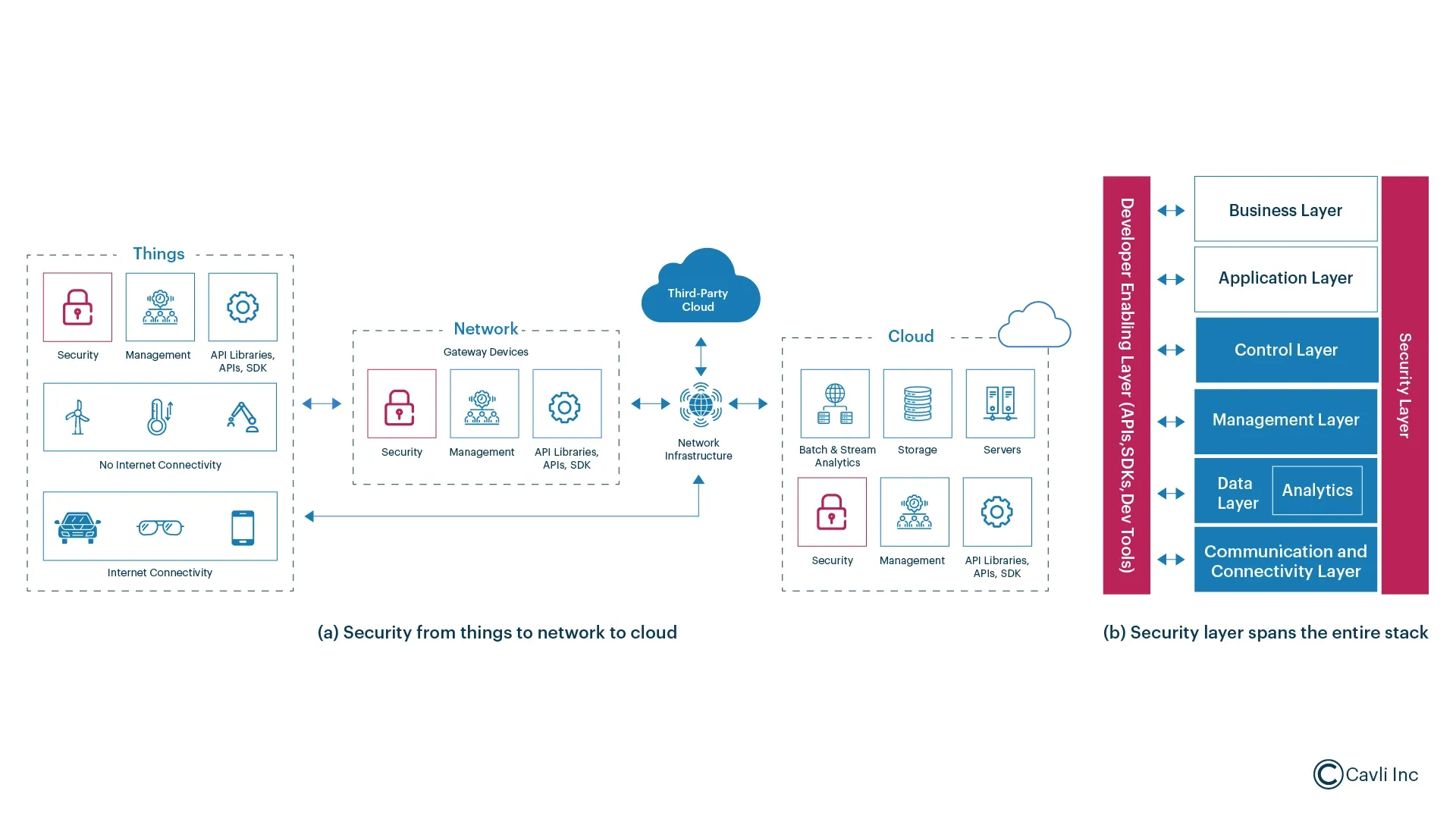
Components of IoT Security
This section covers various components for securing Internet of Things (IoT) environments, including device security, data protection, network security, and more.
IoT Device Security
IoT device security ensures that each device is protected at both the hardware and software levels.
Secure Boot:
Secure boot is a cryptographic process that verifies the device’s firmware integrity and software during startup. A secure boot sequence checks that only authorized and verified code is loaded. Techniques like digital signatures and hash-based verification are used here. Secure boot implementations may either prevent booting or log and alert administrators to unauthorized changes, depending on the system's design and criticality.
Hardware Security Modules (HSMs):
HSMs provide a secure environment to store cryptographic keys and perform encryption/decryption operations. IoT devices with HSMs are more resistant to tampering, as sensitive data is isolated in a secure area. A Trusted Platform Module (TPM) is a commonly used HSM that provides hardware-based IoT security.
Firmware Over-the-Air (OTA) Updates:
OTA updates are essential for maintaining IoT device security without physical access. These updates allow manufacturers to patch vulnerabilities remotely. Cryptographic verification ensures the authenticity of the update files, while rollback protection prevents attackers from installing older, vulnerable firmware versions.
Data Security
Securing IoT environments involves IoT data protection (of the device at rest and in transit) and controlling its access with IoT management platforms.
Data Encryption
Encryption ensures the confidentiality and integrity of IoT data as it is transmitted and stored.
AES (Advanced Encryption Standard):
AES is an IoT security standard commonly used to encrypt data at rest. AES-256 provides a high level of security with relatively low processing requirements, making it suitable for IoT.
TLS/SSL (Transport Layer Security / Secure Sockets Layer):
These protocols secure data in transit, ensuring that information sent between devices and servers is encrypted. TLS 1.3 is the preferred protocol for all new deployments due to its improved security features and efficiency. Support for TLS 1.2 should be maintained only in legacy systems or scenarios where compatibility constraints exist.
Access Control
Access control ensures that only authorized users and devices can interact with IoT systems.
Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC):
These methods control access in IoT networks. In RBAC, permissions are granted based on the user's role, while ABAC considers various attributes (e.g., user location, device type) to dynamically allow or deny access in an IoT management platform.
OAuth 2.0:
OAuth is an open-IoT security standard authorization protocol that allows IoT applications to grant access to users without exposing credentials and manages secure API access.
Data Integrity
Data integrity ensures that IoT data remains accurate, unaltered, and trustworthy throughout its lifecycle.
Cryptographic Hash Functions:
Hashing algorithms like SHA-256 are used to verify that data has not been altered. A hash is calculated before transmission and compared with a hash generated upon receipt to detect tampering.
HMAC (Hash-Based Message Authentication Code):
HMAC is an enhanced form of hashing that includes a secret key, making it harder for attackers to manipulate data without accessing the key.
Network Security
Network security is critical in IoT protection, as these devices often communicate over a variety of networks, including Wi-Fi, cellular, and mesh networks. Network security aims to protect the data as it travels across these channels.
Firewalls:
Firewalls filter incoming and outgoing traffic based on predefined security rules. Deep Packet Inspection (DPI) firewalls analyze the data packets at a granular level, enabling more sophisticated filtering in IoT security services.
Network Segmentation:
VLANs (Virtual Local Area Networks):
VLANs logically segment IoT devices from other parts of the network. Network segmentation limits the spread of potential attacks, particularly when proper access controls and routing restrictions are in place to prevent unauthorized communication between VLANs.
Microsegmentation:
For more granular control, microsegmentation breaks the IoT network into small, isolated segments, often using software-defined networking (SDN). This makes lateral movement across the network more challenging for attackers and securing IoT devices.
Secure Communication Protocols:
MQTT with TLS:
MQTT (Message Queuing Telemetry Transport) is a lightweight protocol widely used in IoT. Securing MQTT with TLS encrypts the communication and can provide authentication when combined with client certificates or other authentication mechanisms. MQTT brokers can also use username-password authentication and client certificate authentication.
CoAP with DTLS:
CoAP (Constrained Application Protocol) is often used in constrained IoT environments. Datagram Transport Layer Security (DTLS) is a version of TLS adapted for UDP, which is suitable for CoAP-based IoT devices.
Identity and Access Management (IAM)
IAM controls who or what is allowed to access IoT resources, ensuring that only trusted users and devices can interact within the system.
Device Authentication
Device authentication ensures that devices can verify their identity before participating in the IoT network.
PKI (Public Key Infrastructure):
PKI issues digital certificates to IoT devices, allowing them to verify each other’s identities before communicating. PKI-based systems use public-private key pairs and rely on certificate authorities (CAs) to verify device identities.
Mutual TLS Authentication:
This approach requires both the client and server to authenticate themselves. It’s often used in high-security IoT applications, such as industrial control systems, where trust is critical.
User Authentication
User authentication ensures that only authorized individuals can access IoT resources.
Multi-Factor Authentication (MFA):
MFA adds a second layer of authentication (such as a temporary passcode or biometric data) to verify the identity of users accessing IoT systems, reducing unauthorized access risks.
Authorization Policies
Authorization policies define the specific permissions granted to users and devices within the IoT system.
Fine-Grained Access Controls:
Policies that specify what actions users and devices can perform in the IoT system. Fine-grained control may be implemented via ABAC, which checks specific attributes (e.g., device type or location) before granting access.
Zero Trust Model:
A Zero Trust security approach assumes no implicit trust. Every device, user, and network segment must be verified continuously before being granted access to resources as part of strict IoT cybersecurity rules.
Vulnerability and Threat Management
This component is crucial for identifying, assessing, and addressing vulnerabilities and threats that could compromise IoT systems.
Vulnerability Scanning:
Automated tools scan IoT devices, software, and network configurations for known vulnerabilities. Open-source tools like OpenVAS or proprietary solutions like Qualys provide regular vulnerability reports, which are essential for maintaining IoT security.
Penetration Testing:
Manual testing by security experts to simulate real-world attacks. Penetration testing identifies weaknesses that automated scans might miss, particularly those unique to IoT devices, such as protocol misconfigurations.
Automated Patch Management:
This involves automatically deploying patches to IoT devices as vulnerabilities are discovered. Patch management systems track patching status, schedule updates, and ensure that patches are applied consistently.
Privacy and Compliance
Privacy and compliance ensure that IoT systems adhere to data protection standards and regulations, such as GDPR, CCPA, and HIPAA.
Data Minimization:
IoT devices are configured to collect only the data necessary for their intended function. Minimizing data collection reduces exposure to privacy risks and aligns with Privacy by Design principles.
Anonymization and Pseudonymization:
Anonymization:
Data is altered so that individuals cannot be identified, even with additional data. This process is often irreversible.
Pseudonymization:
Data is masked in a way that it can still be attributed to an individual but only through additional information. This approach allows some flexibility, as data can be re-identified if needed for legitimate purposes.
Compliance Monitoring:
Automated tools regularly assess IoT systems for compliance with privacy regulations. These tools flag potential violations, such as collecting data without consent, and provide reports to demonstrate compliance during audits.
Physical Security
Physical security ensures that devices, particularly those in exposed or remote locations, are protected against physical threats, including tampering, theft, and environmental hazards.
Tamper-Evident Seals and Enclosures:
Some IoT devices include tamper-evident seals or enclosures that show visible signs if someone tries to open or alter them. Tamper-evident designs often use resin-coated screws or tamper-resistant casings.
Environmental Monitoring:
Sensors can monitor environmental conditions (e.g., temperature, humidity) to detect threats such as overheating, water damage, or tampering. In industrial IoT, environmental monitoring is often integrated with alerts to ensure device safety.
Remote Deactivation:
For sensitive devices, remote deactivation can prevent further use if tampering is detected. For example, ATMs or payment terminals can automatically shut down if unauthorized access is detected, mitigating IoT security risks.
Security Analytics and Monitoring
Analytics and continuous monitoring enable the detection of potential security incidents in real-time, allowing a quick response.
Behavioral Analytics:
This technique examines user and device behaviors to detect irregular activities, such as logging in from unfamiliar locations or access attempts outside of regular hours. Behavioral analytics helps identify threats based on abnormal patterns rather than specific rules.
Real-Time Alerts and Incident Response:
SIEM (Security Information and Event Management):
SIEM tools collect and analyze log data in real-time. SIEM systems analyze log data, performing anomaly detection and behavior-based analysis, in addition to triggering alerts based on predefined conditions.
SOAR (Security Orchestration, Automation, and Response):
SOAR systems go a step further by automatically responding to detected threats and blocking IP addresses or isolating devices.
IoT Security Architecture
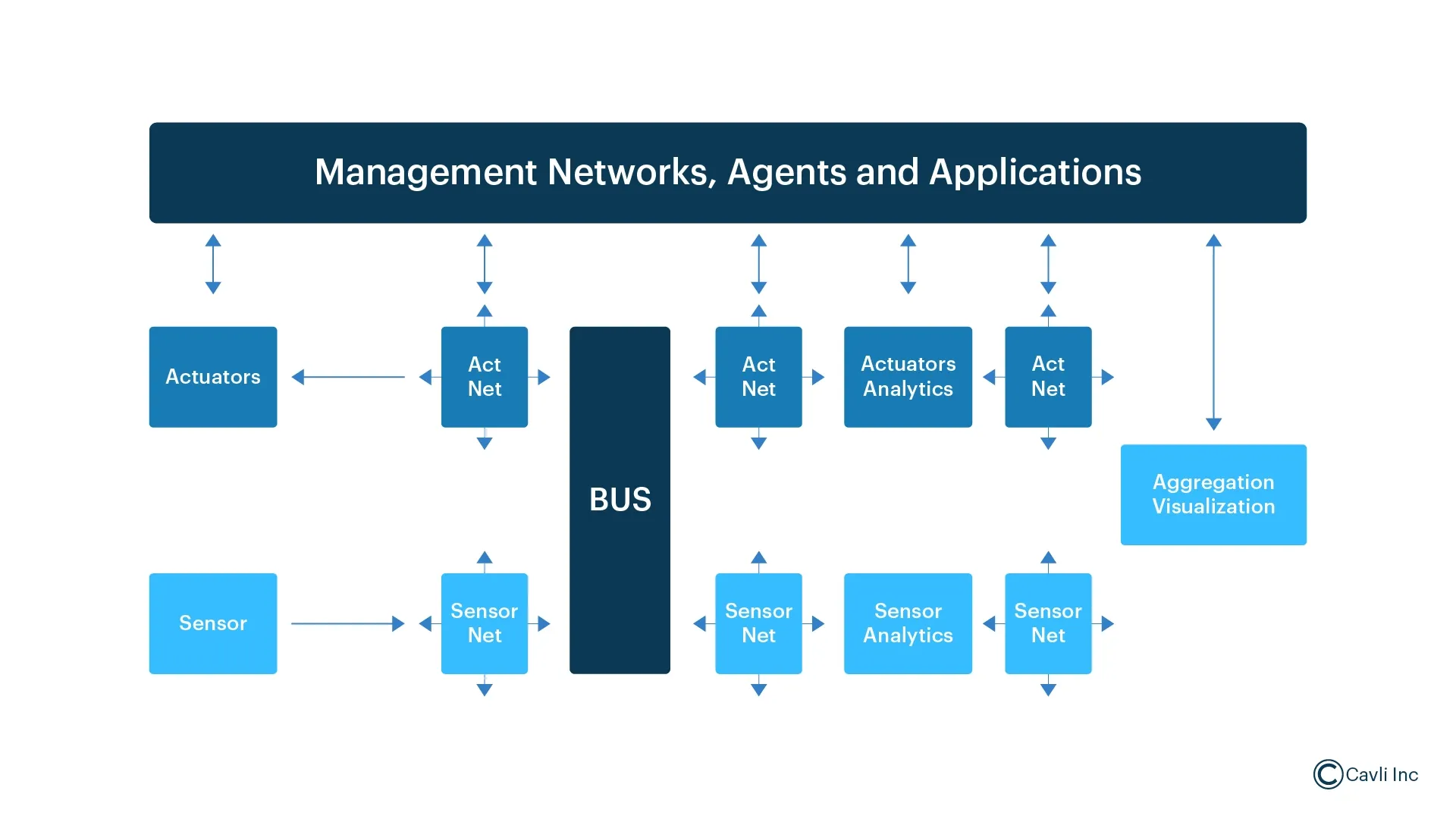
The IoT security architecture involves multiple layers and components to ensure the integrity, availability, and confidentiality of IoT systems. Below are key components of this architecture that contribute to securing IoT ecosystems:
1. Sensors and Actuators
Sensors and actuators are entry points in IoT systems, where data is either collected from or transmitted to the physical world. Securing these devices is crucial to prevent tampering and ensure that data from sensors is accurate and that commands to actuators are genuine.
Unsecured sensors could be manipulated to provide false data, and actuators could be hijacked to perform unauthorized actions.
2. Sensor Net and Act Net
These networks connect sensors and actuators to other parts of the IoT ecosystem. By isolating sensor and actuator networks, it’s easier to control data flow and prevent unauthorized access. They can use encryption, authentication, and secure communication protocols to protect data integrity and prevent unauthorized control of devices.
Without secure communication channels, attackers could intercept or manipulate data in transit, causing data breaches or unauthorized device control.
3. Analytics (Sensor and Actuator Analytics)
Data processing in the sensor analytics and actuator analytics layers can include security checks, anomaly detection, and performance monitoring. Analytics can identify irregular patterns or malicious behavior, helping to detect security threats.
Analytics systems without security measures could be vulnerable to data manipulation, impacting decision-making and potentially triggering harmful actions.
4. Management Networks, Agents, and Applications
This layer acts as the central control system for managing and securing the entire IoT network. It sets policies, enforces access control, and ensures secure device management, updates, and communication. Security agents and applications in this layer monitor the network, respond to incidents, and enforce compliance.
If this central management layer is compromised, it could allow attackers to control multiple devices, disable security policies, or manipulate the system at scale.
5. BUS (Central Communication Pathway)
The BUS, such as VCAN, SPI, MQTT, Modbus, etc., facilitates secure communication between various components. In an IoT network security context, it would ensure that data moving across the network is encrypted and authenticated, preventing unauthorized access to the communication channel.
If the BUS is not secured, attackers could intercept communications or inject malicious commands, potentially impacting multiple devices simultaneously.
6. Aggregation and Visualization
This component aggregates data and provides real-time visualization, giving administrators insights into the IoT system's current status. Security dashboards in this layer can help monitor device activity, track anomalies, and display alerts, enabling rapid response to security incidents.
A compromised visualization system could lead to incorrect conclusions or obscure critical security events, potentially delaying response times.
Why is IoT Architecture Important to IoT Security?
The IoT architecture emphasizes segregated networks, centralized management, and secure communication channels. These are essential elements in IoT management to prevent unauthorized access, maintain data integrity, and detect anomalies. Here’s a summary of its relevance:
Network Isolation and Segmentation
By separating sensor and actuator networks, the IoT architecture reduces the risk of lateral movement, limiting the spread of attacks.
Centralized Management and Monitoring
Having a central layer for managing devices, networks, and policies ensures that security updates, access control, and monitoring can be consistently applied and managed.
Real-Time Analytics and Anomaly Detection
Sensor and actuator analytics help detect anomalies in real time, identifying potential security threats through data analysis and monitoring device behavior.
Secure Data Aggregation and Visualization
Providing secure, real-time insights into device performance, security events, and system health enables administrators to quickly respond to potential security threats.
Reduces Attack Surface
The segmented and layered structure minimizes the attack surface by isolating functions, which is especially relevant in IoT systems with numerous devices and endpoints.
IoT Information Security Challenges in a Connected Ecosystem
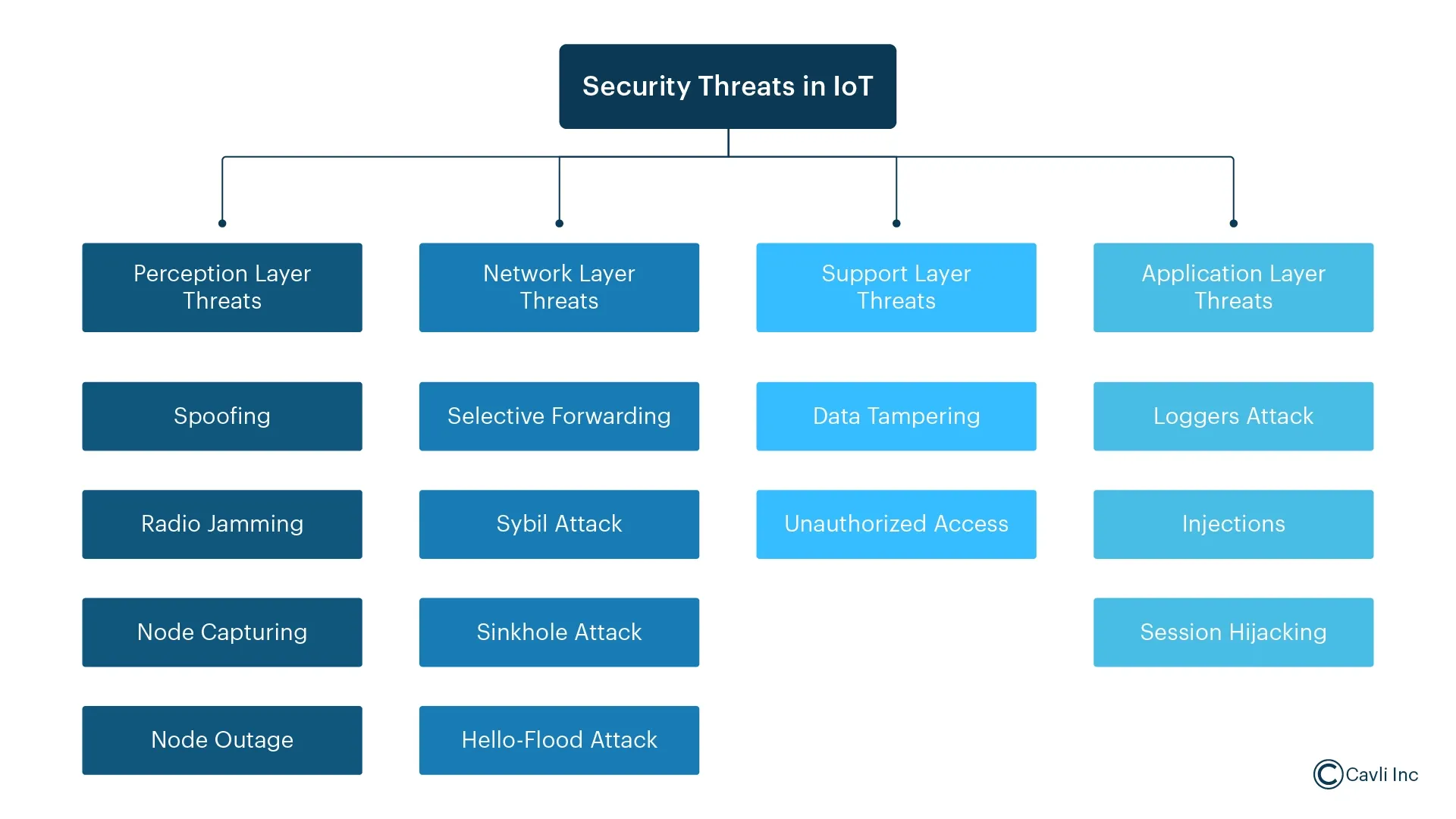
1. Resource Constraints
IoT devices are often limited in processing power, memory, and battery life, making it difficult to implement robust security measures. Complex encryption and continuous monitoring can drain resources, and smaller devices may lack the capacity for advanced security protocols.
2. Lack of Standardization
The diversity in IoT devices, protocols, and manufacturers leads to inconsistent security practices and interoperability issues. With no universal security standards, it’s challenging to enforce consistent protection across devices, leaving systems vulnerable when connecting products from different vendors.
3. Update and Patch Management
Many IoT devices lack mechanisms for regular software updates, leaving them exposed to known vulnerabilities. Some devices require manual updates, which can be impractical in large or remote deployments, increasing the risk of long-term security gaps.
4. Physical Access Risks
IoT devices are often deployed in public or remote locations, exposing them to tampering or theft. Physical access can allow attackers to extract data, disable devices, or bypass security controls, especially when devices lack tamper-resistant designs.
5. Scalability
The large scale of IoT deployments, especially in industrial and city infrastructure applications, makes security management complex. With thousands or even millions of devices in operation, it’s challenging to monitor, update, and secure each one effectively. Scalability requires automated solutions for monitoring, updates, and threat detection, but many IoT ecosystems lack these capabilities.
6. Privacy Concerns
IoT devices collect vast amounts of data, including sensitive personal information, which raises privacy concerns. Inadequate data protection or unauthorized data collection could lead to privacy violations, especially with regulations like GDPR and CCPA requiring strict data handling practices. Ensuring compliance and managing data privacy are challenging when devices are constantly collecting and transmitting data.
7. Supply Chain Risks
IoT devices are often manufactured using components from multiple suppliers across various countries. This can create security vulnerabilities if any part of the supply chain is compromised. Attackers could potentially introduce malware or other vulnerabilities during the manufacturing process, which could then be exploited later. Verifying the security of every component in the supply chain is complex but essential for secure IoT deployment.
8. Insider Threats
The risk of insider threats is often overlooked in IoT security. Insiders with knowledge of the IoT system, such as employees or contractors, can misuse their access to compromise the system. Strong access controls, monitoring, and policies are required to minimize these risks, but implementing these measures across distributed IoT devices is challenging.
Mirai Botnet Attack (2016): The Mirai botnet stands as one of the most notorious examples of cyberattacks involving Internet of Things (IoT) devices. In 2016, it orchestrated one of the largest recorded distributed denial-of-service (DDoS) attacks. By exploiting weak security measures, particularly default login credentials, Mirai compromised hundreds of thousands of IoT devices, including cameras and routers. These compromised devices were then weaponized to flood targeted websites and online services with excessive traffic. High-profile victims included major platforms like Twitter and Netflix, resulting in significant disruptions and highlighting vulnerabilities in IoT security.
Mitigation Measures and Best Practices in IoT Security
As IoT ecosystems continue to expand, implementing robust security measures is paramount. Below are detailed mitigation strategies and best practices to address IoT security challenges effectively.
1. Secure Device Design
Securing the device at the design level is the first step toward ensuring the safety of the IoT ecosystem. Below are measures that can be implemented during the device design phase:
Secure Boot
Secure boot processes are vital to ensure that devices only run trusted software during the boot-up process.
Implement Cryptographic Verification:
Ensure that devices boot using only trusted and verified firmware. Establish a chain of trust from the hardware root of trust to the application layer.
Use Digital Signatures:
Sign firmware with digital certificates. Verify signatures during the boot process to prevent unauthorized code execution.
Hardware Security Modules (HSMs) and Trusted Platform Modules (TPMs)
HSMs and TPMs offer robust solutions for securely storing cryptographic keys and performing cryptographic operations.
Secure Key Storage:
Utilize HSMs or TPMs to store cryptographic keys securely. Protect sensitive information from physical attacks and side-channel attacks.
Enable Secure Cryptographic Operations:
Offload cryptographic computations to HSMs to enhance security without burdening the main processor.
Lightweight Encryption and Security Protocols
Using resource-efficient encryption methods is essential for IoT devices with constrained resources.
Implement Resource-Efficient Encryption:
Use algorithms like AES-128, ChaCha20, or Elliptic Curve Cryptography (ECC) suitable for constrained devices.
Adopt Datagram Transport Layer Security (DTLS):
Secure communication for devices using UDP-based protocols like CoAP.
2. Robust Authentication and Access Control
Robust authentication and access control mechanisms are essential to prevent unauthorized access to IoT systems.
Strong Device Authentication
Authentication methods ensure that only authorized devices can connect and interact with the network.
Use Certificates and PKI:
Implement X.509 certificates for mutual authentication between devices and servers. Employ a robust Public Key Infrastructure (PKI) for certificate management.
Token-Based Authentication:
Utilize OAuth 2.0 or JSON Web Tokens (JWT) for device authentication where appropriate.
Multi-Factor Authentication (MFA)
MFA strengthens security by requiring multiple forms of verification before granting access to IoT systems.
Enhance User Authentication:
Require at least two forms of verification for user access to IoT systems. Combine something the user knows (password), something they have (security token), or something they are (biometrics).
Access Control Models
Access control ensures that only authorized users and devices can access specific resources or services within an IoT system.
Role-Based Access Control (RBAC):
Assign permissions based on user roles to enforce the principle of least privilege.
Attribute-Based Access Control (ABAC):
Grant access based on user attributes, environmental conditions, or resource sensitivity.
3. Data Encryption and Protection
Protecting data through encryption is a key aspect of securing an IoT environment, both when data is in transit and at rest.
Encryption of Data in Transit and at Rest
Encrypting data ensures that sensitive information remains confidential even if intercepted or accessed by unauthorized parties.
Use TLS/SSL Protocols:
Secure data in transit using the latest versions of TLS (preferably TLS 1.3).
Encrypt Stored Data:
Implement AES-256 or equivalent encryption for data at rest on devices and servers.
End-to-End Encryption (E2EE)
E2EE ensures that data is encrypted from the point of origin to the final destination, preventing unauthorized access along the way.
Protect Data Across the Entire Path:
Ensure that data is encrypted from the point of origin to the final destination. Prevent intermediaries from accessing or altering the data.
Secure Key Management
Proper key management is essential for maintaining the confidentiality and integrity of encrypted data.
Protect Cryptographic Keys:
Store keys securely using HSMs or TPMs. Implement key rotation and renewal policies to minimize exposure if a key is compromised.
4. Firmware and Patch Management
Keeping firmware and software up to date is critical for addressing vulnerabilities and preventing security breaches.
Over-the-Air (OTA) Updates
OTA updates allow devices to be updated remotely, ensuring they stay secure without requiring physical access.
Enable Remote Updates:
Implement secure OTA mechanisms to deploy firmware updates without physical access.
Ensure Update Authenticity:
Use cryptographic signatures to verify the integrity and authenticity of update packages.
Automated Patch Management
Automating the deployment of patches ensures timely updates to address vulnerabilities.
Regularly Deploy Security Patches:
Schedule automatic updates to address vulnerabilities promptly.
Monitor Update Processes:
Keep logs and alerts for update failures or anomalies.
Rollback Protection
Ensuring that devices cannot be downgraded to insecure versions is important for maintaining security over time.
Prevent Downgrades to Vulnerable Versions:
Implement measures to block the installation of older, insecure firmware.
5. Network Security and Segmentation
Network security and segmentation techniques are essential to isolate and protect IoT devices from potential attacks and vulnerabilities.
Network Segmentation and VLANs
Network segmentation helps isolate IoT devices from critical infrastructure, reducing the impact of potential security breaches.
Isolate IoT Devices:
Separate IoT devices from critical networks using VLANs or network segments.
Implement Micro-Segmentation:
Use software-defined networking (SDN) to create granular network segments for enhanced security.
Zero Trust Architecture
A zero-trust approach ensures that every device and user must be verified continuously before accessing the network.
Continuous Verification:
Assume no implicit trust; verify every device and user attempting to access resources.
Enforce Strict Access Controls:
Limit network access based on identity, device health, and context.
Secure Communication Protocols
Using secure communication protocols ensures that data exchanged between devices remains safe and private.
Use Secure Versions of Protocols:
Implement MQTT over TLS and CoAP with DTLS.
Regularly Update Protocols:
Stay current with protocol updates and patches to address known vulnerabilities.
6. Anomaly Detection and Monitoring
Real-time monitoring and anomaly detection are crucial to identifying and mitigating security threats in IoT systems.
Real-Time Monitoring and Alerts
Real-time monitoring systems are essential for continuously tracking device activities and identifying any unusual behavior that could indicate a potential attack.
Deploy SIEM Systems:
Collect and analyze security events across the IoT ecosystem.
Set Up Real-Time Alerts:
Configure alerts for suspicious activities or policy violations.
Anomaly Detection
By implementing anomaly detection techniques, IoT systems can automatically flag deviations from normal device or user behavior, potentially indicating a security threat.
Implement AI and Machine Learning:
Use behavioral analytics to detect deviations from normal device or user behavior.
Identify Security Threats:
Detect potential threats like data exfiltration, DDoS attacks, or device hijacking.
Intrusion Detection and Prevention Systems (IDPS)
IDPS are designed to monitor network traffic and detect potential intrusions or malicious activities.
Monitor Network Traffic:
Use IDPS to identify and block malicious activities.
Employ Deep Packet Inspection:
Analyze packet contents for known attack signatures.
7. Physical Security Measures
Physical security is crucial for protecting IoT devices from tampering, theft, and other physical attacks that may compromise their functionality or data.
Tamper-Evident Design
Devices should be designed to resist tampering or, at the very least, make such tampering detectable.
Use Protective Enclosures:
Design devices with tamper-resistant casings and seals.
Implement Tamper Detection:
Equip devices with sensors to detect physical intrusion or manipulation.
Secure Deployment Environments
Ensuring the security of the physical locations where IoT devices are deployed is key to preventing theft or tampering.
Control Physical Access:
Install devices in secure locations where possible.
Use Lockable Enclosures:
Protect devices in public or vulnerable areas with lockable or durable housings.
Environmental Monitoring
Environmental monitoring can help detect physical threats such as changes in temperature, humidity, or physical intrusion.
Detect Physical Threats:
Install sensors to monitor temperature, humidity, and other environmental factors.
Set Up Alerts:
Configure notifications for environmental changes that may indicate tampering.
8. Privacy Compliance and Data Management
Privacy and data protection are critical to maintaining the trust of users and complying with regulations.
Data Minimization
Collecting only the necessary data helps reduce the risk of exposure and ensures compliance with data protection regulations.
Collect Only Necessary Data:
Limit data collection to what is essential for device functionality.
Avoid Excessive Data Storage:
Regularly review and purge unnecessary data.
Data Anonymization and Pseudonymization
Anonymizing or pseudonymizing data can help protect personal information and reduce privacy risks.
Protect Personal Data:
Apply techniques to anonymize or pseudonymize sensitive information.
Comply with Privacy Regulations:
Ensure practices align with GDPR, CCPA, HIPAA, and other relevant laws.
Regular Compliance Audits
Conducting periodic reviews and audits ensures ongoing compliance with privacy regulations and best practices.
Conduct Periodic Reviews:
Audit data handling and storage practices.
Maintain Compliance Documentation:
Keep detailed records of compliance efforts and findings.
9. Secure Supply Chain and Component Verification
Ensuring the security of the supply chain is vital to prevent vulnerabilities from being introduced at any point during device production or software development.
Component Authentication
Verifying the authenticity of hardware components and software ensures that they meet security standards and are free from vulnerabilities.
Verify Hardware Integrity:
Use cryptographic techniques to authenticate hardware components.
Implement Secure Bootloaders:
Ensure that only authorized firmware can run on the device.
Trusted Suppliers and Partners
Working with trusted suppliers who follow stringent security standards can reduce the risks posed by insecure components.
Conduct Due Diligence:
Work with suppliers who adhere to industry security standards.
Supply Chain Transparency:
Require transparency in the sourcing and manufacturing processes.
Secure Firmware and Software
Validating firmware and software before deployment ensures they are free from vulnerabilities and malicious code.
Validate Pre-Installed Software:
Verify that firmware and software are free from malicious code before deployment.
Monitor for Unauthorized Changes:
Use checksums or hashes to detect modifications to software components.
10. Education and Training
Ongoing education and training for both users and developers is essential to maintaining a strong security posture in an IoT environment.
User Education
Promoting security awareness among users ensures they understand the importance of securing their IoT devices and networks.
Promote Security Awareness:
Educate users on the importance of changing default passwords and securing their networks.
Provide Clear Instructions:
Offer guidance on configuring devices securely.
Security Training for Development Teams
Development teams must be well-versed in secure coding practices to avoid introducing vulnerabilities during device development.
Implement Secure Coding Practices:
Train developers on secure coding standards and common vulnerabilities.
Conduct Regular Security Assessments:
Encourage code reviews and security testing throughout the development lifecycle.
Incident Response Plans
Having an incident response plan in place is essential to quickly address any security breaches or threats.
Develop Response Strategies:
Create detailed plans for responding to security incidents.
Regularly Update and Test Plans:
Conduct drills and update plans based on new threats or organizational changes.
11. Future-Proofing Security Measures
Preparing for emerging threats and technological advances ensures that IoT systems can adapt to the evolving landscape of cybersecurity challenges.
Prepare for Emerging Threats
Staying informed about new technologies and threats helps organizations plan for potential future security risks.
Stay Informed on Advances:
Monitor developments in quantum computing and emerging cryptographic techniques.
Plan for Scalability:
Design systems that can accommodate new security measures as they become necessary.
Adopt Security by Design Principles
Building security into the design phase ensures that security is a fundamental part of the system from the outset.
Integrate Security Early:
Include security considerations from the initial design phase.
Perform Threat Modeling:
Identify potential threats and vulnerabilities early in the development process.
Engage with Security Communities
Collaborating with industry peers allows organizations to stay informed and share insights on the latest security trends and threats.
Participate in Industry Groups:
Join organizations like the Industrial Internet Consortium (IIC) or the IoT Security Foundation.
Share and Receive Threat Intelligence:
Collaborate with peers to stay ahead of emerging threats.
Closing Notes:
IoT security is a critical field that requires a multi-layered approach to safeguard connected devices, sensitive data, and networks. As IoT systems continue to expand in both scale and diversity, the risks associated with resource constraints, lack of standardization, physical vulnerabilities, and data privacy challenges have become more pronounced.
By embracing best practices and fostering security awareness across development, management, and user levels, organizations can build a secure IoT environment that meets both operational needs and regulatory standards, enabling the safe and responsible growth of IoT technology in a connected world.
Ace your Connectivity Game with Cavli C-Series IoT Connectivity Modules

Go Beyond and Explore
What are the best practices for implementing Secure Boot in IoT devices to ensure firmware integrity?
Secure Boot is a critical security measure for IoT devices, verifying the integrity of the firmware at startup using cryptographic techniques. Best practices include using digital signatures to authenticate firmware, establishing a chain of trust from the hardware root of trust to the application layer, and employing rollback protection to prevent the installation of outdated or compromised firmware versions.
How can IoT systems effectively utilize VLANs and microsegmentation to enhance network security?
VLANs and microsegmentation play a crucial role in network security by logically isolating IoT devices from other network segments. Best practices include configuring VLANs to separate sensitive device traffic and using software-defined networking (SDN) for microsegmentation to create finer-grained security boundaries, thereby reducing the attack surface and limiting the spread of potential network intrusions.
Can you describe the application of Multi-Factor Authentication (MFA) in securing IoT environments and its impact on reducing unauthorized access?
MFA is vital for enhancing user authentication in IoT systems by requiring multiple forms of verification (something the user knows, has, or is) before granting access. Implementing MFA helps mitigate the risk of unauthorized access due to stolen credentials, significantly enhancing security in environments where device control and data sensitivity are high.
What strategies should be adopted for secure key management in IoT devices to protect data encryption keys from exposure?
Secure key management is foundational for maintaining the confidentiality and integrity of encrypted data in IoT devices. Strategies include using Hardware Security Modules (HSMs) or Trusted Platform Modules (TPMs) for storing cryptographic keys securely, implementing key rotation policies to minimize the impact of key compromise, and ensuring that key management processes are resilient to physical and side-channel attacks.
How do advanced IoT security architectures incorporate anomaly detection and real-time monitoring to address emerging cyber threats?
Advanced IoT security architectures leverage behavioral analytics and machine learning to monitor and analyze device and user behaviors for signs of anomalies, which could indicate a security threat. Real-time monitoring, supported by Security Information and Event Management (SIEM) systems, facilitates immediate detection of unusual activities and automated responses, enhancing the system's ability to thwart attacks before they cause significant damage.

