What is Deep Packet Inspection?
Do your routers or gateways have a backdoor, causing critical information leaks?
DPI, meaning Deep Packet Inspection,is a sophisticated network security process that involves inspecting the content of data packets as they travel through firewalls/network checkpoints. DPI is an advanced data processing method essential for identifying, or blocking packets with specific data or malicious codes, ensuring robust dpi network security.
Deep Packet Inspection or Deep packet analysis method enables real-time, detailed analysis and management of network traffic, enhancing both network security and performance. By employing deep packet inspection, organizations can monitor and analyze internet traffic at various network checkpoints with packet filtering, effectively preventing cyber threats and optimizing data flow across their networks.
The Evolution Explained: From Conventional Packet Analysis to Deep Packet Inspection
Deep Packet Inspection began to gain prominence in the early 2000s. One of the earliest widespread implementations of DPI was in the realm of network security and telecommunications. ISPs (Internet Service Providers) started using DPI extensively for monitoring and managing network traffic, ensuring network security and compliance, as well as for traffic shaping and prioritizing certain types of data over others.
DPI was also employed for regulatory compliance, such as enforcing content restrictions or detecting copyright infringement online. As deep packet analysis technology advanced, its applications expanded into enterprise networks for similar purposes like network inspection, traffic management, and policy enforcement.
Earlier, a more basic packet filtering known as Conventional Packet Analysis was used for network monitoring. In conventional packet analysis, the focus is primarily on the headers of the packets traveling through a network. Conventional packet analysis examines source and destination IP addresses, port numbers, protocol types, and other header metadata to determine the route and basic purpose of the traffic.
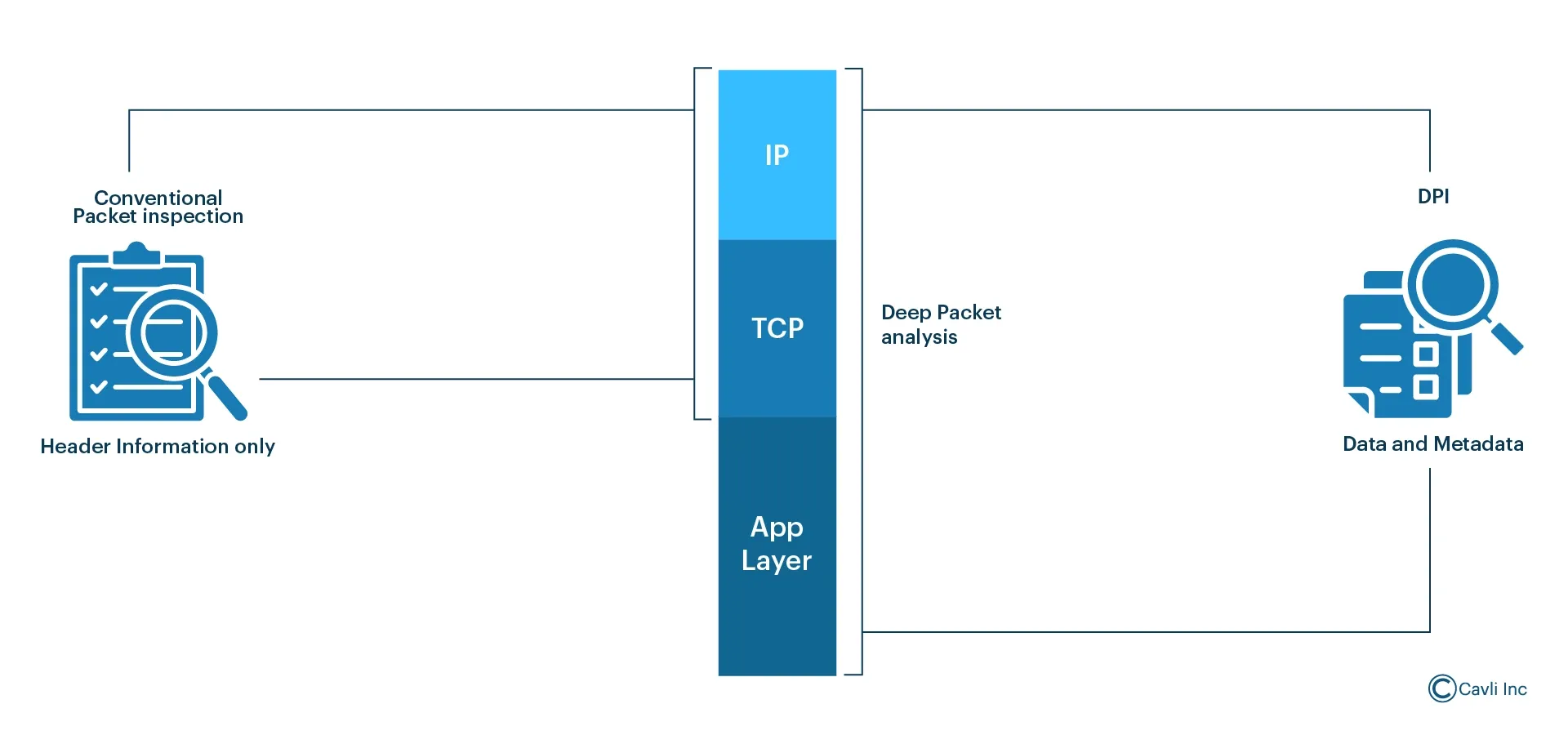
Deep packet inspection in comparison to conventional packet inspection
Deep Packet Inspection, on the other hand, is a real-time deep packet analysis, analyzing both the header and payload of data packets in the internet traffic. Unlike conventional packet analysis, Deep Packet Inspection delves deeper and analyzes both the header and payload of data packets, accessing the source IP address, destination, and also a comprehensive understanding of the applications, protocols, and data being transmitted.
Inspecting Payload with Deep Packet Inspection
Deep Packet Inspection (DPI), or deep packet analysis, inspects the payload of network packets. It enables the examination of data transmitted within various layers of the OSI model, offering detailed insight into network traffic. The layers analyzed include:
Application-Layer Data
DPI inspects data from specific applications such as HTTP, FTP, or SSH. This helps in identifying and managing application-specific traffic efficiently.
Protocol-Layer Data
This includes analyzing data associated with specific protocols, such as DNS, SMTP, or SIP. DPI tools can detect unusual behaviors or threats by monitoring these protocol interactions.
Payload Data
DPI examines the actual data being transmitted, such as files, emails, or chat messages. This allows for content-based filtering, threat detection, and policy enforcement.
Types of Packet Inspection Levels
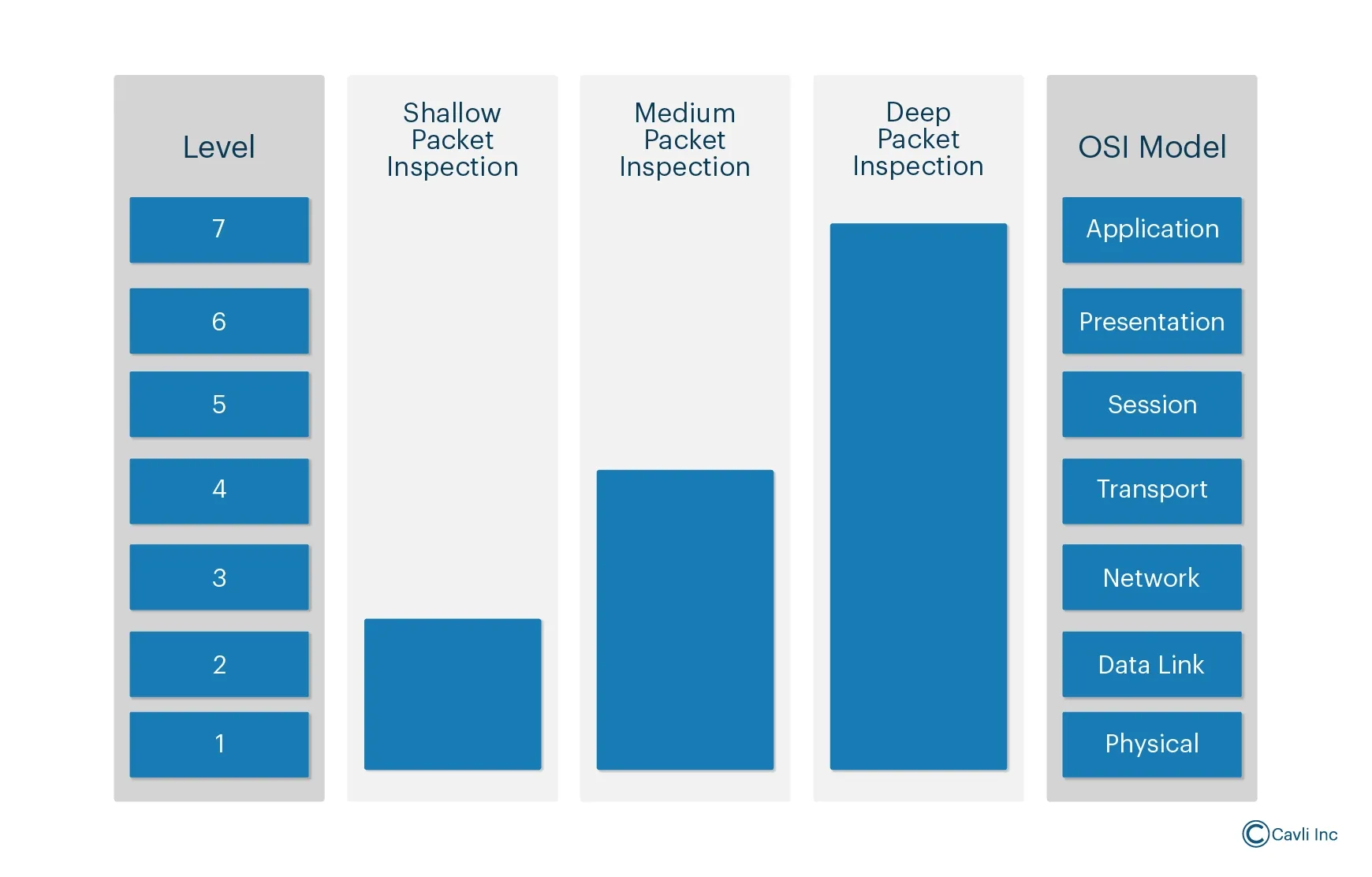
Types of Packet Inspection Levels
Different packet inspection levels are depicted here.
1. Shallow Packet Inspection (SPI)
Shallow Packet Inspection or SPI examines only the header of the packet, such as the source and destination IP addresses, protocol type, and port number. SPI is relatively fast but provides limited information compared to Deep Packet Inspection.
2. Medium Packet Inspection (MPI)
Medium Packet Inspection goes a step further by examining both the packet header and parts of the payload. MPI is commonly used in application proxies to filter traffic based on content types and data formats.
3. Deep Packet Inspection (DPI)
DPI inspects the entire packet, including the header and payload. It can identify specific applications, protocols, and even the nature of the data. This kind of deep packet analysis allows for precise traffic management and security enforcement.
Detecting Protocols and Applications with Deep Packet Inspection
Deep Packet Inspection (DPI) employs advanced methods to identify protocols and applications by analyzing network traffic. The techniques used include Port Detection, Signature Detection, and Heuristic Detection, each contributing to a comprehensive deep packet analysis.
1. Port Detection
Port Detection examines the source and destination port numbers of a packet to identify the protocol or application in use. For example:
- HTTP typically uses port 80.
- FTP uses port 21.
By inspecting these ports, DPI can quickly categorize and identify traffic types for better network management.
2. Signature Detection
Signature Detection involves searching for specific patterns or "signatures" in the packet payload to identify protocols or applications. These signatures act as unique "fingerprints" for known applications, enabling DPI tools to precisely match traffic against a database of predefined signatures.
3. Heuristic Detection
Heuristic Detection uses rules of thumb or behavioral analysis to identify the protocol or application based on factors like the packet's payload, headers, and timing. While many DPI tools rely on Signature Detection, Heuristic Detection complements it by recognizing new or evolving protocols without predefined signatures. This approach enhances the adaptability of deep packet analysis in dynamic network environments.
Techniques Used for Deep Packet Inspection
Deep Packet Inspection (DPI) employs various techniques to analyze and manage network traffic. These techniques enhance network security and traffic monitoring by identifying patterns, anomalies, and potential threats.
1. Pattern Matching
Pattern Matching is a DPI technique used to detect specific sequences of bytes or packet characteristics in network traffic. It is widely utilized in:
- Intrusion Detection Systems (IDS)
- Antivirus software
This technique involves comparing incoming data packets against a database of known patterns or "signatures" to identify potential threats, such as:
- Malware signatures
- Malicious URLs
By matching traffic with known signatures, Pattern Matching strengthens DPI network monitoring and threat detection.
2. Protocol Anomaly Detection
Protocol Anomaly Detection identifies deviations from standard, expected protocol behaviors. Each network protocol (e.g., HTTP, FTP, TCP) has defined standards that specify compliant traffic characteristics.
Detection tools monitor internet traffic to identify anomalies that may indicate security threats, such as:
- Malware activity
- Protocol-based attacks
- Unauthorized access
Examples of anomalies include:
- Unexpected or illegal commands
- Incorrect packet sizes
- Violations of protocol standards
3. Intrusion Prevention System (IPS)
An Intrusion Prevention System (IPS) is a DPI technique that provides network security by actively preventing threats. Unlike an Intrusion Detection System (IDS), which only detects and alerts on potential threats, an IPS takes proactive actions, such as:
- Dropping malicious packets
- Blocking traffic from offensive sources
- Alerting administrators about suspicious activity
IPS operates using various detection methods, including:
- Signature-based detection: Matching specific patterns in traffic
- Anomaly-based detection: Identifying deviations from normal behavior
- Stateful protocol analysis: Monitoring the state of network sessions
This technique enhances DPI capabilities by not only identifying threats but also preventing their impact in real-time.
How Does Deep Packet Inspection Work?
Deep Packet Inspection (DPI) operates at multiple layers of the OSI model, focusing particularly on the Application layer for network inspection and packet analysis. This enables DPI firewalls to identify and analyze the content of data packets, such as their source (IP address) and destination. DPI tools detect and monitor user activity and enforce security policies based on the data packet content.
Imagine information being sent over a network. The information is first converted into data packets, and these packets then undergo the following process flow at DPI firewalls in computer networks:
1. Data Capturing
The first stage in the deep packet analysis process is data capturing. DPI tools capture data packets as they pass through network inspection points, such as routers, switches, or DPI firewalls. High-speed packet capture technologies are employed for packet filtering and ensuring real-time analysis.
2. Deep Packet Analysis
Once a data packet is captured, deep packet analysis dissects and extracts both header and payload information. DPI tools apply techniques such as signature matching, Intrusion Prevention System (IPS) analysis, and protocol anomaly detection to understand the content and context of the traffic.
3. Decision-Making
Based on the deep packet analysis, DPI solutions make real-time decisions on how to handle the traffic. Actions include:
- Allowing or blocking data traffic
- Prioritizing specific types of data
- Redirecting data packets for further inspection
These decisions are enforced through network policies, which can be customized by network administrators.
Applications of Deep Packet Inspection
1. Network Security
DPI is vital for detecting and preventing malware and intrusions. By examining packet content, DPI firewalls identify malicious code, abnormal traffic patterns, and potential security breaches. It is used in:
- Intrusion Detection and Prevention Systems (IDPS)
- Network-based antivirus systems
These capabilities enable real-time threat detection and mitigation, protecting networks from cyberattacks and unauthorized access.
2. Network Management
DPI significantly enhances bandwidth optimization and Quality of Service (QoS) enforcement. By identifying and prioritizing different types of traffic, DPI ensures critical applications receive adequate bandwidth while limiting non-essential traffic. This improves network performance and user experience.
3. Compliance
Organizations must comply with data privacy and security regulations. DPI helps monitor data flows to ensure adherence to these requirements. It can identify and block unauthorized data transfers, ensuring sensitive information is handled in line with legal and organizational policies.
4. Data Loss Prevention (DLP)
DPI protects sensitive data from leaks and breaches by inspecting outgoing traffic. It detects and prevents unauthorized transmission of confidential information, such as intellectual property, financial data, and personal details.
5. Monitoring and Surveillance
DPI is utilized by both governments and enterprises for monitoring and surveillance purposes. Governments employ DPI to detect and prevent illegal activities, such as terrorism and cybercrime. Enterprises use it to monitor employee activities, enforce acceptable use policies, and safeguard intellectual property.
6. Quality of Service (QoS)
DPI is essential in QoS systems for prioritizing certain types of traffic, such as voice or video. This ensures these traffic types receive sufficient bandwidth and maintain low latency, enhancing their reliability and performance.
Importance of Deep Packet Inspection in IoT Security
The Internet of Things (IoT) has revolutionized how devices communicate and interact, bringing about significant benefits in various sectors, from smart homes to industrial automation. However, the proliferation of IoT devices also introduces substantial security risks. IoT devices often lack robust security features, making them vulnerable to attacks. Deep Packet Inspection is essential in securing IoT networks by providing granular visibility into the data traffic, detecting anomalies, and preventing malicious activities.
How DPI is Applied to IoT Traffic
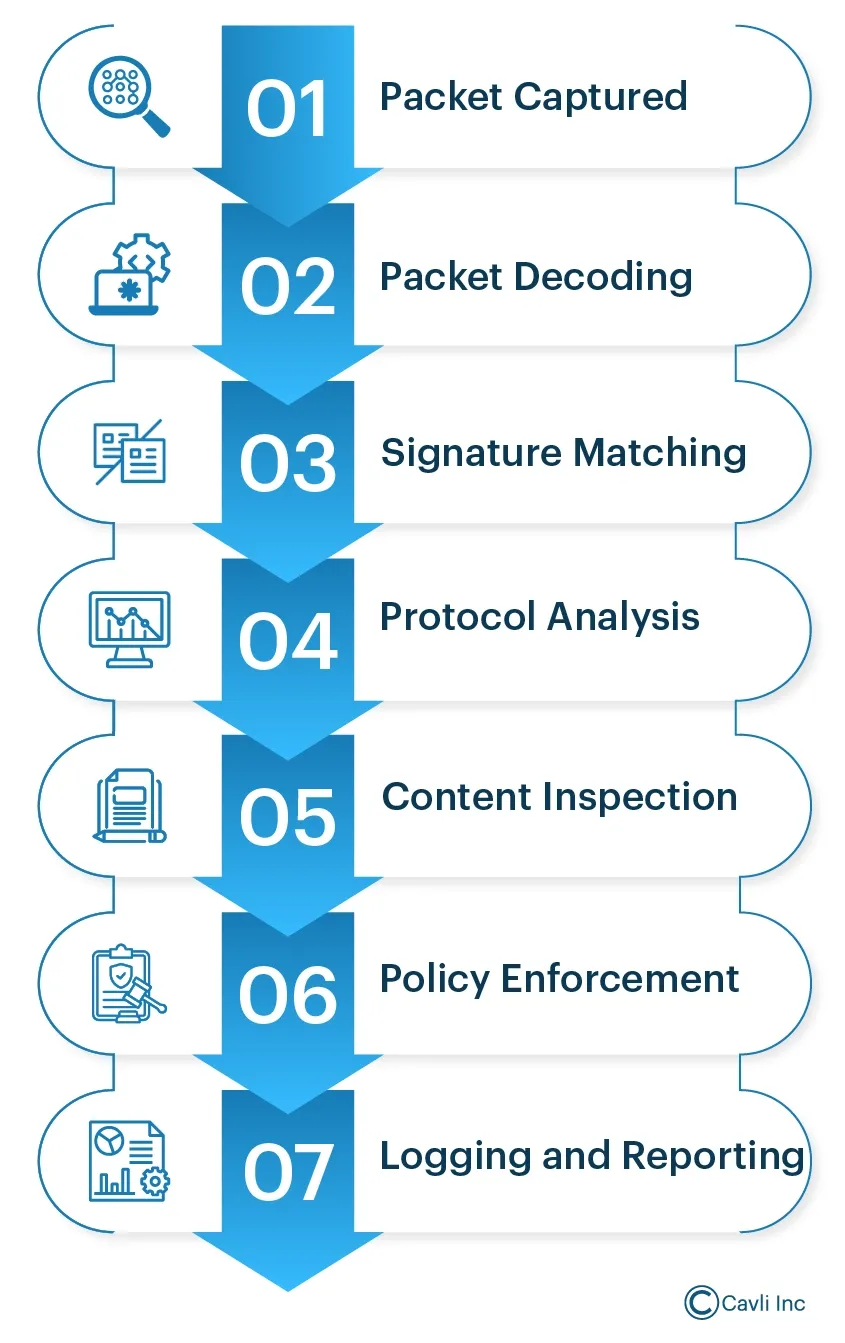
Types of Packet Inspection Levels
DPI in IoT involves several steps to ensure comprehensive traffic analysis:
Packet Capture
The data packets get intercepted between the IoT device and the cellular network at various points like DPI appliances or routers and switches. In this initial interception, the DPI system can operate in different modes, including inline mode (where it sits directly in the path of traffic) or in passive mode (where it monitors traffic without affecting the flow).
The goal of packet capture is to gather all necessary data for further inspection without introducing significant latency or packet loss. DPI solutions enable real time DPI network monitoring for data packets in the IoT ecosystems. Deep packet inspection with packet capture technologies like Wireshark, tcpdump, Snort etc., handle large volumes of data generated by IoT devices without causing latency or performance issues.
Packet Decoding
Once a packet is captured, the DPI system decodes it to extract its components including header and payload. This process begins with parsing the packet header to understand the basic network information, such as source and destination IP addresses, port numbers, and protocol type (e.g., TCP, UDP, ICMP).
The system then moves to the payload, which contains the actual data being transmitted. Packet decoding involves recognizing and interpreting the structure of different higher layer protocols (e.g., HTTP, HTTPS, DNS) to correctly identify the type of communication and its intended purpose.
Signature Matching
After decoding, the DPI system compares the packet's content against a database of predefined signatures. These signatures are patterns or rules that represent known network behaviors, applications, or security threats. Signature matching is a crucial step for detecting and identifying network traffic that aligns with known threats or behaviors.
The system might use various techniques, including keyword searches, regular expressions, or heuristics, to perform this matching. Signature matching in a cellular IoT context is critical for ensuring that the IoT module is not transmitting or receiving malicious data, which could compromise the device or the larger network it is part of.
Protocol Analysis
Protocol analysis occurs if a signature match is found, where the DPI system delves deeper into the identified protocol to confirm and further analyze the traffic. This step involves examining the specific attributes and behaviors of the protocol in question. For instance, if an IoT sensor sends periodic updates via MQTT, the DPI system will ensure that these updates are consistent with the established protocol behavior and do not exhibit signs of tampering or misuse.
Content Inspection
Content inspection involves a deeper analysis of the packet's payload, particularly when dealing with encrypted or compressed data. In the case of encrypted traffic (e.g., HTTPS), the DPI system may use techniques like SSL/TLS decryption (assuming proper permissions and certificates) to view the underlying data. Content inspection is critical for identifying sensitive information (e.g., credit card numbers, personal data), malware, or unauthorized file transfers.
Policy Enforcement
After analyzing the packet, the DPI system applies predefined policies or rules to determine how to handle the traffic. These policies are typically defined by network administrators and can range from simple actions like blocking or allowing traffic to more complex actions like QoS prioritization, traffic shaping, or redirecting traffic for further inspection. Policy enforcement is crucial to maintaining the security and efficiency of the IoT network, ensuring that only authorized and necessary communication takes place.
Logging and Reporting
Finally, the DPI system logs detailed information about each inspected packet, including metadata like source and destination addresses, protocol type, detected application, and any actions taken during policy enforcement. These logs are essential for various purposes, such as network monitoring, security analysis, troubleshooting, and compliance auditing. The data can be visualized in reports, providing insights into network usage patterns, potential security threats, and the effectiveness of applied policies.
Role of Deep Packet Inspection in IoT Applications
Smart Cities
Smart cities utilize a vast network of IoT sensors and connected devices to manage urban infrastructure efficiently. These applications include:
Traffic Management
DPI helps analyze data from traffic sensors in real time, optimizing traffic flow and reducing congestion. By monitoring data packets, DPI can prioritize emergency vehicle communication and detect anomalies, such as unexpected traffic patterns or accidents.
Public Safety
DPI enhances the security of surveillance systems and emergency response networks. It ensures that data from cameras and emergency systems is transmitted securely and efficiently, preventing unauthorized access into the networks.
Environmental Monitoring
Smart cities deploy numerous sensors to monitor air quality, water quality, and weather conditions. DPI ensures the integrity and reliability of this data, enabling timely and accurate environmental assessments and responses.
Utility Management
DPI monitors data from smart grids and utility meters, ensuring secure and efficient energy distribution. It can detect and prevent fraudulent activities, such as hacked utility meters.
Healthcare
IoT in healthcare, also known as the Internet of Medical Things (IoMT), includes medical devices, wearables, and health monitoring systems that collect and transmit patient data.
Data Security
DPI ensures that sensitive patient data, such as vital signs and medical records, are transmitted securely between IoT devices and healthcare systems to protect against data breaches and unauthorized access.
Compliance
Healthcare applications must comply with regulations like HIPAA (Health Insurance Portability and Accountability Act). DPI helps maintain compliance by monitoring data flows and ensuring that only authorized devices and personnel can access sensitive information.
Device Integrity
DPI monitors the behavior of medical devices, ensuring they operate within normal parameters. It can detect and mitigate potential cyber threats, such as malware or unauthorized firmware updates, which could compromise patient safety.
Quality of Service (QoS)
DPI prioritizes critical medical data transmissions, ensuring that real-time health monitoring and emergency communications are not delayed or disrupted by less critical network traffic.
Industrial IoT (IIoT)
Industrial IoT involves the use of connected devices and sensors in manufacturing and industrial processes to increase efficiency, productivity, and safety.
Network Security
DPI secures industrial control systems (ICS) by monitoring and analyzing data packets for signs of cyberattacks. It can detect and block malicious traffic aimed at disrupting critical infrastructure.
Operational Efficiency
DPI helps manage and prioritize data traffic from various industrial sensors and devices, ensuring that critical control commands and transmits data without delay.
Preventative Maintenance
By analyzing data from IoT sensors, DPI can detect early signs of equipment failure or inefficiency. This allows for proactive maintenance, reducing downtime and improving overall operational efficiency.
Compliance and Reporting
Many industrial sectors are subject to strict regulations regarding data security and operational safety. DPI aids in compliance by providing detailed monitoring and reporting capabilities, ensuring that all regulatory requirements are met.
Connected Vehicles
Connected vehicles rely on IoT technology for a variety of functions, including navigation, infotainment, vehicle-to-vehicle (V2V) communication, and vehicle-to-infrastructure (V2I) communication.
Communication Security
DPI secures the communication channels between vehicles and infrastructure, ensuring that data such as navigation instructions and safety alerts are transmitted securely and reliably.
Data Integrity
DPI ensures that data from vehicle sensors and control systems is accurate and has not been tampered with, which is crucial for the safety and efficiency of autonomous driving systems.
Threat Detection
DPI can detect and mitigate cyber threats targeting connected vehicles, such as hacking attempts or malware designed to disrupt vehicle operations.
Performance Optimization
By analyzing data traffic patterns, DPI can help optimize the performance of connected vehicle networks, ensuring that critical updates and communications are prioritized and delivered promptly.
Challenges in Implementing Deep Packet Inspection
High Risk Exposure
The process of DPI involves handling a large amount of data, which can be a target for cyberattacks. If not properly secured, it can lead to data breaches, exposing sensitive user information. There’s also a high risk of DPI being used to exploit data for malicious purposes or to sell user information without consent.
User Privacy Issues
Deep Packet Inspection raises significant privacy concerns due to its ability to scrutinize the content of data packets. By examining the payload, DPI can uncover sensitive information such as personal communications, financial details, and browsing habits.
This level of intrusion can lead to potential misuse of data, unauthorized surveillance, and breaches of confidentiality. Users may feel their privacy is being compromised, leading to a lack of trust in network providers.
Net Neutrality Implications
Using Deep Packet Inspection (DPI) in IoT applications raises net neutrality concerns, as it can prioritize specific types of data traffic. This capability can lead to unfair treatment of certain services, creating a two-tiered internet where some applications receive faster, prioritized access while others are slowed down.
Additionally, ISPs might engage in paid prioritization, giving preference to IoT service providers who can afford to pay for better performance. This practice exacerbates the issue, potentially stifling innovation and competition.
Regulatory and Legal Challenges
The deployment of DPI technologies is subject to various regulatory and legal challenges. Different countries have distinct laws regarding data privacy, surveillance, and cybersecurity, making it complex to implement DPI uniformly.
Compliance with regulations such as the General Data Protection Regulation (GDPR) in Europe requires careful handling of personal data and explicit user consent. Its capability to intercept and analyze data packets must align with these legal frameworks to avoid violations and potential penalties.
Closing Notes
The ethical deployment of DPI requires a careful approach that respects user privacy, adheres to regulatory requirements, and maintains the principles of net neutrality. By balancing network security benefits with ethical considerations, DPI can be a powerful tool for protecting and optimizing networks without compromising fundamental rights and freedoms.
Looking ahead, the future of DPI network security is promising. As cyber threats become more sophisticated, it will continue to evolve, incorporating advanced technologies such as machine learning and artificial intelligence to enhance threat detection and response. The increasing adoption of encrypted traffic and the proliferation of IoT devices will drive further innovation in DPI solutions, ensuring that networks remain secure and efficient.

