James, Jr. Network Engineer
Hey Adam, I've been hearing a lot about LwM2M lately. Our team is exploring protocols for a new IoT project, and I’m wondering how it stacks up against MQTT. Why is LwM2M considered unique?
Adam, Sr. Network Engineer
MQTT is fantastic for lightweight messaging in IoT, but LwM2M is built specifically for device management. Think of MQTT as a messaging app, while LwM2M is more like a remote control system designed for efficiently managing devices. It includes features like monitoring, firmware updates, and configuration management while highly optimized for resource-constrained IoT devices.
James, Jr. Network Engineer
That’s interesting! But wouldn’t adding all these device management features make it more resource-intensive and complex to use?
Adam, Sr. Network Engineer
It’s quite the opposite! Lightweight M2M is purpose-built to be lightweight. It uses efficient binary encoding and operates over CoAP—a RESTful, lightweight version of HTTP. Standardized interfaces for operations like firmware updates, monitoring, and configuration make it easier to implement without needing to build these features from scratch.
James, Jr. Network Engineer
That sounds promising for our project. Is it easy to implement, and what security measures does it include?
Adam, Sr. Network Engineer
LwM2M includes built-in security via DTLS, which ensures encrypted communication, device authentication, and data integrity. Implementation is straightforward, particularly with modern IoT modules that often support LwM2M natively. Let me outline the features that make it a strong candidate for IoT device management.
As James begins to grasp the significance of Lightweight M2M in IoT device management, let's dive deeper into this protocol that’s revolutionizing how we manage connected devices. Whether you're developing smart meters, industrial sensors, or asset tracking solutions, understanding LwM2M protocol is crucial for efficient IoT deployment.
What is LwM2M?
Lightweight Machine-to-Machine (LwM2M) is an open mobile industry standard developed by the Open Mobile Alliance (OMA) specifically for IoT device management. LwM2M protocol provides a complete framework for managing device lifecycles, from deployment to decommissioning.
Lightweight Machine-to-Machine (LwM2M) is directly connected to Machine-to-Machine (M2M) communication as a protocol designed to facilitate and optimize M2M communication in IoT (Internet of Things) environments.
The lightweight M2M protocol provides a standardized protocol for M2M communication. It uses a lightweight architecture based on the Constrained Application Protocol (CoAP), which is optimized for devices with limited resources (low power, memory, or processing capability).
Lightweight M2M Protocol Includes Capabilities for:
- Device configuration
- Firmware updates
- Fault diagnostics
- Monitoring and control
Lightweight M2M protocol ensures secure communication using DTLS (Datagram Transport Layer Security), enabling secure data transmission between devices and servers.
Key Features of LwM2M
Object-Based Resource Model
An object-based resource model is a hierarchical and structured approach for organizing and representing data.
For example, consider a temperature sensor. Here the temperature sensor is the object.
The resources are data points associated with an object (Temperature Sensor). The object has resources, such as Current Temperature, Maximum Temperature, etc.
The object is a logical group of resources, representing a specific type of data or functionality (e.g., device information, connectivity settings, or firmware updates).
Efficient Communication
- Built on the CoAP (Constrained Application Protocol) which is optimized for constrained environments.
- Uses a binary data format for minimal overhead and reduced bandwidth usage.
- UDP-based communication ensures low latency and minimal network load.
Built-in Device Management
Comprehensive lifecycle management capabilities:
- Remote firmware updates (FOTA) for seamless over-the-air improvements.
- Device configuration for adjusting operational parameters remotely.
- Diagnostics and monitoring for identifying and resolving issues.
- Power management to optimize energy usage in constrained devices.
Security Features
- DTLS-based security for secure communication over constrained networks.
- Device authentication to verify identity before communication.
- Access control mechanisms to ensure only authorized entities can interact with devices.
- End-to-end secure communication channels, established using DTLS, ensure data integrity and privacy over constrained networks.
Advanced Operations
Supports CRUD operations (Create, Read, Update, Delete).Enables advanced features like:
- Execute: Trigger specific functions on devices.
- Observe: Monitor resources in real time for event-driven actions.
- Conditional observations: Notify changes only when specific thresholds are met, improving efficiency.
The Architecture of the LwM2M Protocol
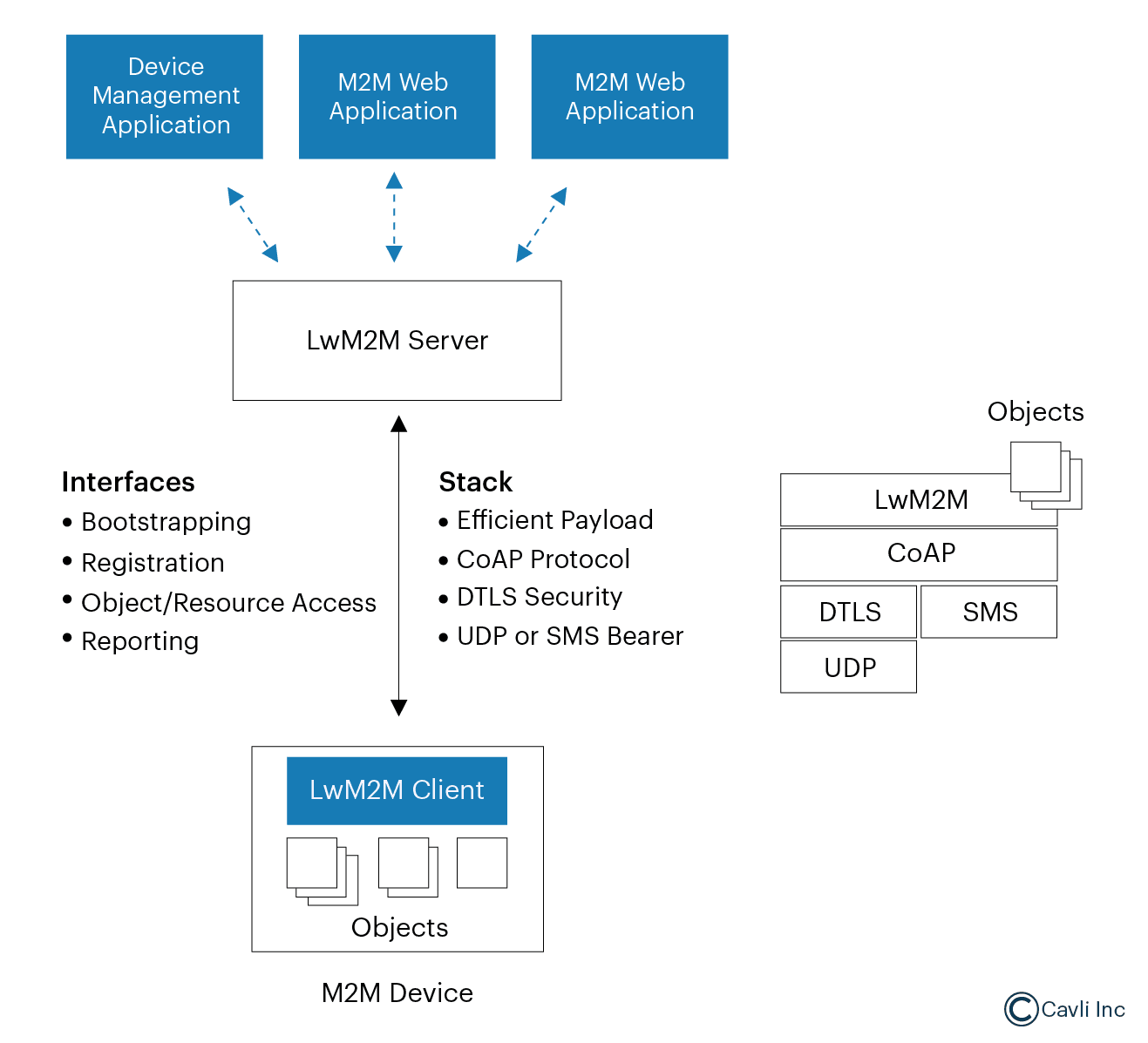
LwM2M follows a client-server architecture consisting of three main components:
- LwM2M Client: The IoT device implementing the client interface
- LwM2M Server: The management system that controls the devices
- LwM2M Bootstrap Server: Responsible for initial device configuration and security setup
LwM2M Client
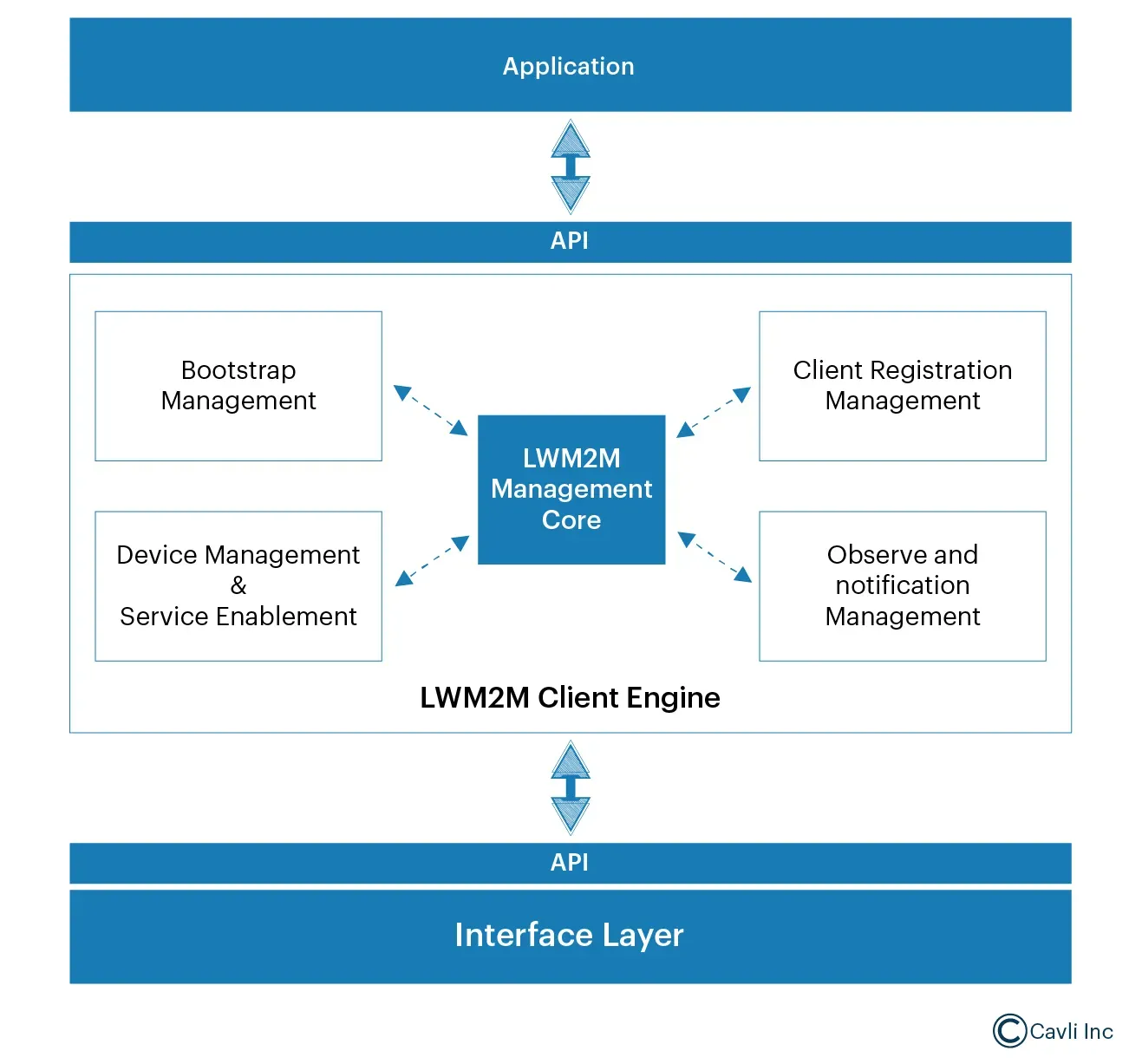
It is a software entity implemented on the IoT device. It manages communication with the LwM2M server and exposes device resources, i.e., provides access to specific functionalities, data, or settings of the device in a standardized way.
LwM2M Server
It is typically hosted in the cloud or on a local network. It manages multiple LwM2M clients by performing operations like monitoring, updating, and controlling devices.
Bootstrap Server
It helps devices connect to the appropriate LwM2M server by provisioning initial configuration details. Bootstrapping in LwM2M involves provisioning IoT devices (clients) with configurations, credentials, and server details. This process enables them to register with the LwM2M server and begin normal operations.
The Four Pillars of LwM2M Interface
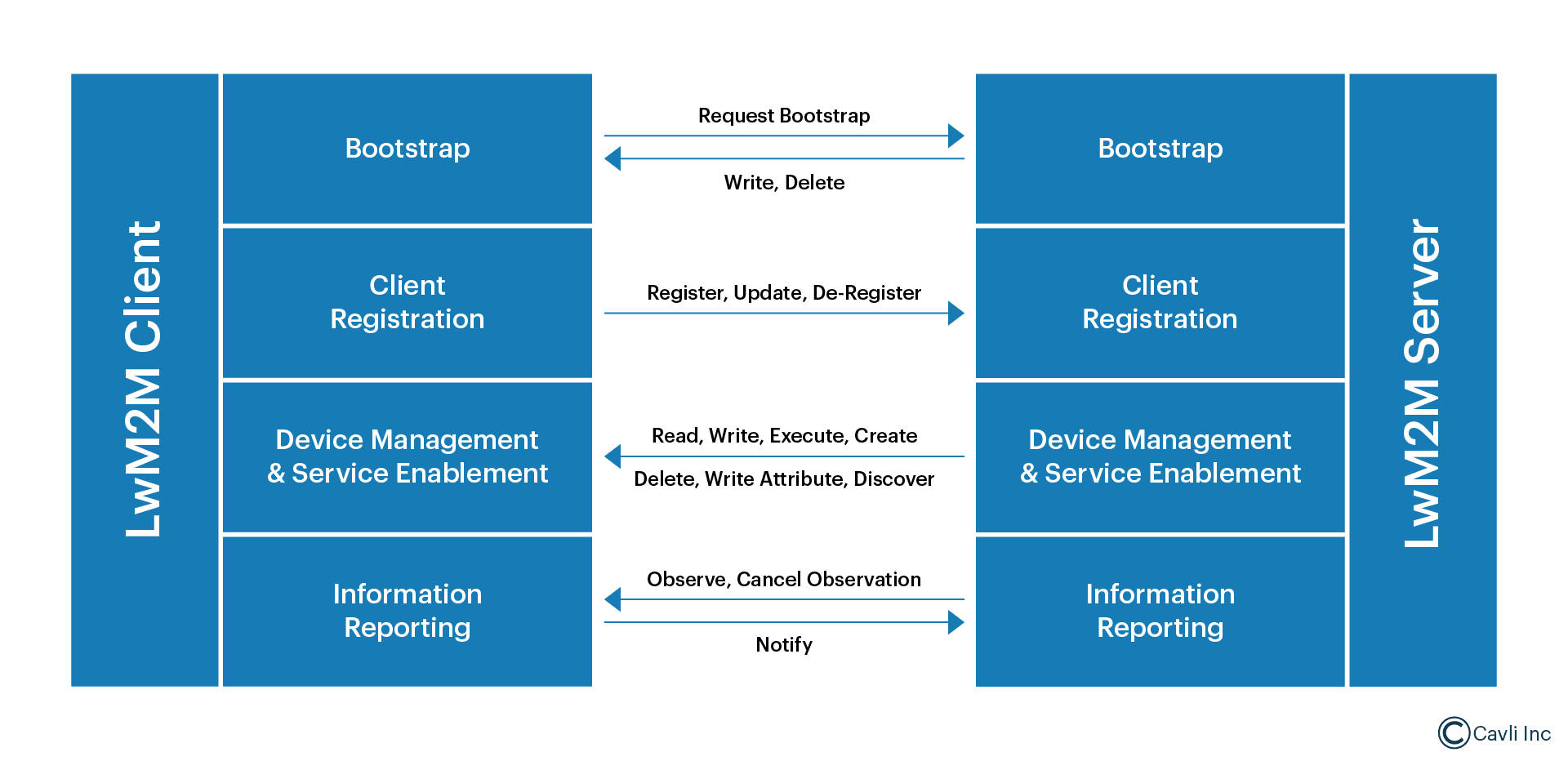
LwM2M protocol defines four essential interfaces that form its operational foundation:
Bootstrap Interface
- Handles initial device setup and security configuration
- Ensures secure connection establishment
- Manages credential distribution
Client Registration Interface
- Enables device registration with the LwM2M server
- Handles device discovery
- Maintains device lifecycle states
Device Management and Service Enablement Interface
- Provides access to device resources
- Manages device configurations
- Enables remote operations
Information Reporting Interface
- Manages data reporting
- Handles resource observations
- Enables notifications and monitoring
IoT Connectivity Protocol Stack
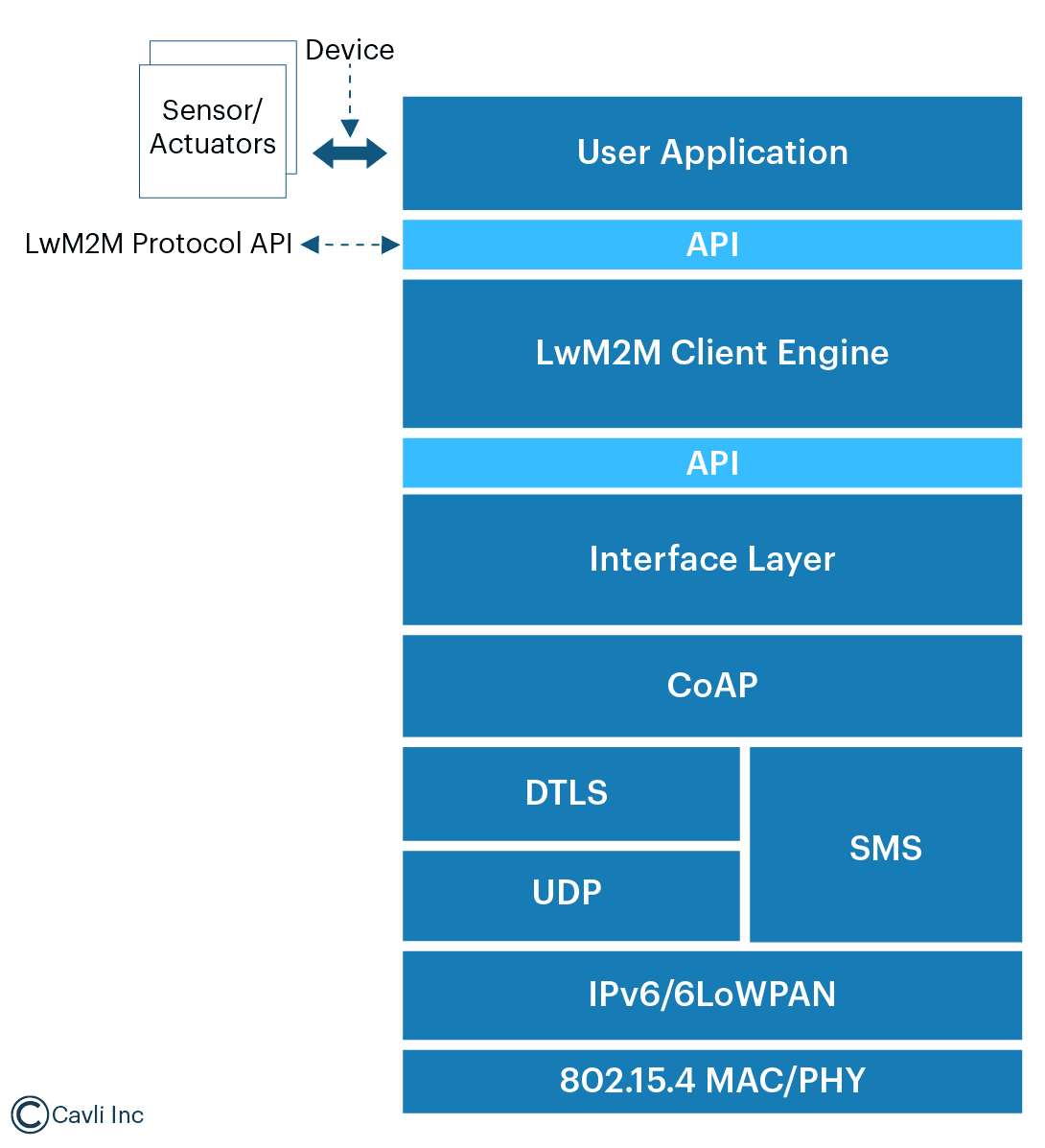
Layers of the IoT Connectivity Protocol Stack
LwM2M Protocol Engine Core
The Protocol Engine Core is the application layer implementing the complete OMA Device Management and Service Enablement operations. It provides Application Programming Interfaces (APIs) for developers to interact with the LwM2M Client and Server efficiently.
Key tasks include:
- Managing objects and resources.
- Coordinating device registration, bootstrapping, and monitoring.
- Handling notifications and updates.
Interface Layer
It implements generic APIs that allow interaction with:
- OMA/IPSO Objects: Standardized objects that define specific device functionalities (e.g., location, firmware update).
- CoAP Protocol: Provides connectivity between client and server.
- Platform-Specific Implementations: Features like Firmware Over-the-Air (FOTA) updates for seamless firmware management.
The interface layer abstracts underlying hardware and connectivity details, ensuring developers can focus on application-level operations.
Constrained Application Protocol (CoAP)
CoAP is a lightweight RESTful protocol that forms the communication backbone between LwM2M clients and servers.
Functions include:
- Message Headers: For defining communication structure.
- Request/Response Codes: Support CRUD (Create, Read, Update, Delete) operations.
- Retransmission Mechanisms: Ensure reliability in low-bandwidth networks.
Note: LwM2M uses only a subset of CoAP features to maintain simplicity and minimize overhead.
Datagram Transport Layer Security (DTLS)
It provides a secure channel for all communication between the LwM2M Client and Server.
Key Security Features include:
- Encryption of data in transit.
- Authentication of devices.
- Protection against tampering or unauthorized access.
Transport Layer: UDP/SMS
UDP (User Datagram Protocol) is the mandatory transport mechanism for LwM2M, and it is indeed chosen for its low overhead and minimal resource requirements.
SMS Binding (Optional): It is used in environments where internet-based communication is unavailable or unreliable.
IPv6/6LoWPAN (Network Layer)
Provides IPv6 support for constrained devices by using 6LoWPAN (IPv6 over Low-Power Wireless Personal Area Networks).
It enables efficient communication in large-scale IoT deployments by optimizing IPv6 packet transmission for resource-constrained environments.
IEEE 802.15.4 MAC/PHY (Physical Layer)
This layer provides the physical and media access control (MAC) protocols for low-power wireless communication.
Typically supplied by chip vendors, it supports wireless sensor networks in IoT systems.
Other IoT Layers in the Protocol Stack
In a broader context, the IoT protocol stack includes additional layers that enhance the functionality and efficiency of IoT systems:
Application Layer
In IoT, this layer interacts with end-users and business processes. Examples include:
- HTTP/HTTPS: Common for web-based IoT applications.
- MQTT/AMQP: Protocols optimized for IoT messaging in cloud environments.
Middleware Layer
Acts as an intermediary, processing data from devices and enabling analytics. Common platforms in this layer include:
- IoT Gateways for local processing.
- Cloud services (e.g., AWS IoT Core, Azure IoT Hub).
Network Layer
Handles communication between devices and servers, often using:
- LPWAN technologies like LoRaWAN or NB-IoT for long-range communication.
- Wi-Fi, Bluetooth, or Zigbee for short-range communication.
- IPv6/6LoWPAN for energy-efficient, scalable networks.
Perception Layer
The bottom layer, consisting of sensors and actuators, enables the physical world to interact with digital systems.
Devices in this layer capture environmental data (e.g., temperature, humidity, motion) or perform physical actions (e.g., turning lights on/off).
Response Codes
| Code | Description | Handling Strategy |
|---|---|---|
| 2.01 | Created | Successful registration/resource creation |
| 2.02 | Deleted | Successful deregistration/resource deletion |
| 2.04 | Changed | Successful update operation |
| 2.05 | Content | Successful read operation |
| 4.00 | Bad Request | Invalid syntax - Check payload format |
| 4.01 | Unauthorized | Authentication failed - Verify credentials |
| 4.04 | Not Found | Resource unavailable - Verify object/resource ID |
| 4.05 | Method Not Allowed | Operation not supported |
| 5.00 | Internal Server Error | Server-side issue - Implement retry mechanism |
Comparison Between Different LwM2M Protocol Versions
| Feature/Aspect | LwM2M 1.0 (2017) | LwM2M 1.1 (2018) | LwM2M 1.2 (2020) | LwM2M 1.3 (2023) |
|---|---|---|---|---|
| Primary Focus | Device management and monitoring for IoT. | Introduced transport flexibility and event-driven communication. | Enhanced scalability, security, and resource handling. | Cloud-ready features and broader use case support. |
| Transport Protocols | UDP (via CoAP). | Introduced support for TCP, SMS, and non-IP transports (e.g., LoRaWAN). | CoAP enhancements like block-wise transfers for large payloads. | Introduced support for HTTP/HTTPS for cloud environments. |
| Data Serialization Formats | TLV (Type-Length-Value), JSON. | Introduced CBOR (Concise Binary Object Representation) for efficiency. | Enhanced JSON and CBOR handling for patch operations. | Advanced JSON usage for cloud-native applications. |
| Object Model | Fixed object model with static objects and resources. | Introduced support for dynamic object creation and deletion. | Extended object definitions and richer resource models. | Continued expansion of object and resource libraries. |
| Security | DTLS with Pre-Shared Keys (PSK) for secure communication. | Introduced certificate-based authentication and raw public key support. | Improved PKI-based security and handling for constrained devices. | Advanced encryption and cloud-based authentication support. |
| Resource Observation | Basic observation model for resource changes. | Enhanced observation for efficient event-driven updates. | Allowed partial updates to specific resources (JSON Patch). | Refined observation and notification for cloud systems. |
| Energy Efficiency | Limited power-saving features (UDP-based). | Introduced queue mode for devices to conserve power. | Improved queue handling for low-power, intermittent devices. | Optimized for edge-to-cloud resource-constrained devices. |
| Scalability | Basic scalability for small IoT networks. | Better scalability with flexible transports and observation. | Scaled to large IoT deployments with enhanced protocols. | Optimized for massive device fleets in cloud ecosystems. |
| Firmware Update Support | Basic support for firmware updates over CoAP. | Introduced support for large firmware updates via block-wise transfers. | More efficient firmware management for constrained devices. | Streamlined for cloud-to-device updates. |
| Interoperability | Focused on device-server communication. | Improved compatibility with non-IP networks. | Extended to multiple device management scenarios. | Cloud and hybrid IoT system integration. |
| Use Cases | Basic IoT device management and monitoring. | Broader IoT applications, including LPWAN devices. | Industrial IoT, smart cities, and large-scale networks. | Cloud IoT platforms, edge computing, and enterprise IoT. |
Understanding LwM2M Real-World Applications
Smart Metering
The protocol's lightweight nature makes it ideal for remote meter reading, allowing utilities to collect real-time consumption data through standardized objects without deploying field personnel.
- LwM2M's secure firmware update mechanism ensures meters can be updated remotely with new features and security patches, maintaining system reliability.
- Through its device management capabilities, the Lightweight M2M protocol enables utilities to remotely configure meter parameters, adjust tariff settings, and optimize performance.
- The protocol's observation and reporting features facilitate continuous monitoring of consumption patterns, helping both providers and consumers make data-driven decisions about resource usage and conservation.
Asset Tracking
- Lightweight M2M protocol enables real-time tracking of assets through its object model, which includes dedicated objects for location data and GPS coordinates.
- The protocol facilitates regular status reporting through its observation and notification mechanisms, allowing devices to send updates about their operational conditions.
- Battery management is streamlined using LwM2M's power management objects, which help monitor and optimize battery life.
- The protocol also supports maintenance scheduling by enabling remote device diagnostics and automated maintenance alerts based on predefined thresholds and device health parameters, ensuring proactive asset maintenance.
Smart Agriculture
- Lightweight M2M protocol enhances smart agriculture by providing a standardized and efficient communication framework for agricultural IoT devices.
- Through LwM2M's lightweight device management capabilities, farmers can easily configure and manage multiple sensors across their fields, monitoring soil conditions, nutrient levels, and pH values with minimal network overhead.
- The protocol's efficient data reporting model enables automated irrigation systems to respond instantly to real-time sensor data, ensuring precise water distribution while conserving resources.
- The protocol's firmware update capabilities allow remote maintenance of agricultural sensors and devices, ensuring they remain current with the latest features for crop monitoring and disease detection.
- LwM2M's resource-efficient design extends the battery life of field sensors, reducing maintenance needs while maintaining continuous monitoring of crop health and environmental conditions.
Closing Notes
Lightweight M2M (LwM2M) is a versatile and efficient protocol designed specifically for managing IoT devices in constrained environments. By leveraging a well-defined architecture and a lightweight protocol stack, including CoAP, DTLS, and UDP/SMS, LwM2M provides secure, scalable, and resource-efficient communication between devices and management servers.
LwM2M is a reliable choice for applications ranging from smart cities and industrial IoT to connected consumer devices. As IoT adoption grows, LwM2M stands out as a protocol that balances the need for functionality and efficiency, making it an essential component of modern IoT solutions.
Amusing Tech Chronicles
Facts and Anecdotes Related to this Edition of Wireless By Design

Smart Home System
Imagine a smart home with multiple devices like thermostats, lights, and security cameras. The LwM2M server is like the central control panel that tracks all connected devices. Each device has its settings (objects) and specific functionalities (resources, such as turning on/off or adjusting brightness). If a new device is added, it registers with the central control, just like an LwM2M client registers with the server.

Garden Watering System
Imagine watering a garden with just one hose; you can only water one area at a time. Now imagine a watering system with multiple hoses (MIMO system) watering several parts of the garden at the same time. Similarly, MIMO sends and receives multiple data streams simultaneously, improving throughput and efficiency.

Library System
LwM2M protocol organizes device data like a librarian categorizes and manages books. Objects are like bookshelves, each containing a category of books. The librarian (LwM2Mserver) manages the library, ensuring books are cataloged, accessible, and up-to-date.
Go Beyond and Explore
What is DTLS, and how does it enhance LwM2M protocol security?
DTLS (Datagram Transport Layer Security) is a security protocol designed to provide encryption, data integrity, and authentication for applications that use datagram-based communication protocols, such as UDP (User Datagram Protocol). It is essentially the equivalent of TLS (Transport Layer Security) for connectionless, low-latency protocols.
In the IoT (Internet of Things) context, DTLS is crucial because many IoT protocols, like CoAP (Constrained Application Protocol)—used by LwM2M—rely on UDP for lightweight communication. DTLS ensures secure communication in these resource-constrained environments.
DTLS (Datagram Transport Layer Security) enhances LwM2M security by providing robust encryption, authentication, and data integrity for lightweight, UDP-based communications commonly used in IoT. It ensures that data exchanged between IoT devices (clients) and servers is encrypted, protecting it from eavesdropping.
DTLS supports mutual authentication using pre-shared keys, certificates, or raw public keys, preventing impersonation and unauthorized access. Additionally, it safeguards data integrity by detecting and blocking any tampering during transmission and protects against replay attacks by verifying message freshness. By securing LwM2M device management, DTLS ensures safe device management, firmware updates, and reliable IoT data transmission.
What are the default ports for LwM2M?
The default ports for LwM2M are based on the underlying CoAP (Constrained Application Protocol), which LwM2M uses for communication. Specifically:
1. UDP Default Port: LwM2M primarily uses UDP port 5683 for standard unencrypted communication.
2. Secure Communication with DTLS: For secure communication, the LwM2M protocol uses UDP port 5684, leveraging DTLS for encryption, authentication, and data integrity.
These ports are well-suited for the lightweight nature of IoT devices, which often rely on efficient UDP communication rather than heavier protocols like TCP. By using these standardized ports, LwM2M ensures compatibility across devices and platforms, making it easier to manage IoT devices securely and reliably in constrained environments.
What is the difference between MQTT-SN and LwM2M?
The primary difference between MQTT-SN (Message Queuing Telemetry Transport for Sensor Networks) and Lightweight M2M lies in their purpose and functionality.
MQTT-SN is a lightweight version of MQTT designed specifically for resource-constrained devices in sensor networks. It focuses on publish-subscribe messaging, enabling devices to send or receive messages through a broker efficiently. MQTT-SN is ideal for applications requiring real-time data exchange, such as telemetry and sensor monitoring.
LwM2M, on the other hand, is a device management and communication protocol. It provides a structured object-based model for managing IoT devices and handling tasks like device configuration, monitoring, firmware updates, and security. LwM2M uses CoAP over UDP for its communication and includes built-in security via DTLS.
While MQTT-SN is geared toward lightweight messaging, LwM2M offers a broader range of features for IoT device management and monitoring.
What are the types of Bootstrapping in LwM2M?
-
Factory Bootstrapping:
- The device is pre-configured during manufacturing with server credentials, security keys, and initial settings.
- No dynamic setup is required after deployment. Suitable for devices with stable configurations or environments. Client-Initiated Bootstrapping:
- The client contacts the bootstrap server after powering on or during a reset.
- Commonly used in resource-constrained devices where the client depends on the server for its configuration. Server-Initiated Bootstrapping:
- The bootstrap server initiates communication with the client and sends the configuration.
- Useful for remote updates or recovering devices that have lost their configuration.


