Have you ever wondered how IoT devices manage secure remote access with minimal resource consumption?
In the rapidly evolving landscape of IoT connectivity, where devices often operate with limited memory and processing power, finding the right balance between security and efficiency is crucial. This is where Dropbear SSH steps in – a lightweight alternative to traditional SSH implementations, specifically designed for environments where resources are at a premium.
Before diving into the Dropbear SH, it is important to understand the basics of SSH protocol or otherwise understand the earlier versions of SSH.
Evolution of Dropbear SSH
Secure Shell Protocol (SSH)
In 1995, Tatu Ylönen (University of Helsinki) established the SSH protocol. This protocol is intended to secure remote access to systems over an untrusted network. It introduced the first key-based authentication. The SSH protocol enabled encryption to replace insecure remote login protocols like Telnet and rlogin. It allows remote command execution and file transfers over a secure connection.
The SSH protocol, or Secure Shell Protocol, is a network protocol that enables secure communication over unprotected networks. It facilitates secure remote access and log-in, command execution, and other network services between the two connected devices.
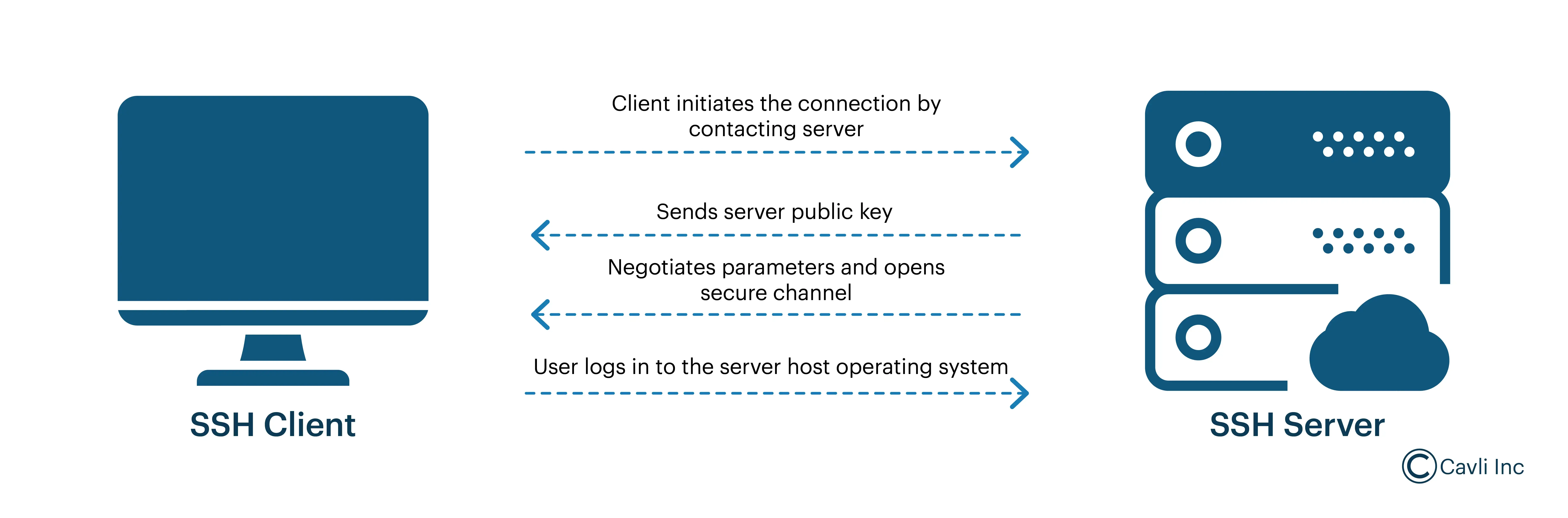
OpenSSH Protocol
OpenSSH came as the open-source alternative to the proprietary SSH in 1999. It eliminated the licensing issues, resulting in widespread adoption. The stand-out features of OpenSSH are
Improved Encryption
Support for stronger ciphers (AES, ChaCha20, etc.).
SH Agent Forwarding
Securely stores and forwards authentication credentials.
X11 Forwarding
Enables running GUI applications over SSH.
SFTP Protocol
Secure alternative to FTP for file transfers.
Chroot Jail Support
Restricts users to specific directories for added security.
Public Key Authentication
Strengthened authentication mechanisms.
OpenSSH is preferred over generic SSH implementations due to its open-source nature, robust security practices, and widespread adoption across Unix-based systems. It provides strong encryption, frequent updates, and excellent interoperability with other systems. Its cost-effectiveness, backed by community-driven support, made it a trusted choice for secure remote communication.
Even though it helped streamline remote server management and enabled secure network tunneling, the large binary size and memory footprint were significant limitations. It led the way to the new and improved Dropbear SSH.
What is Dropbear SSH?
Dropbear SSH is a lightweight and efficient SSH (Secure Shell) server and client designed for embedded systems, network routers, and resource-constrained environments. It prioritizes low memory usage and small binary size while maintaining essential SSH security features, making it ideal for the remote administration of networking devices, industrial systems, and embedded Linux environments.
According to recent embedded systems market analysis, a fraction of IoT devices needing remote access capabilities are choosing lightweight SSH solutions. Dropbear SSH is a perfect candidate with a minimal memory footprint and robust security features.
Key Features of Dropbear SSH
Lightweight
It requires minimal memory and CPU resources, making it ideal for embedded Linux devices, IoT systems, and routers.
Single Binary in Dropbear SSH
Dropbear SSH is lightweight and efficient, particularly for environments with limited resources. One of its notable features is the ability to combine multiple functionalities—SSH server, client, key generator, and key converter—into a single executable binary. This approach simplifies deployment and reduces the overall footprint on the system.
Public Key Authentication
Dropbear SSH supports public key authentication, allowing users to authenticate using SSH keys for secure, password-less access. This method enhances security by eliminating the need for password-based logins. It utilizes a pair of cryptographic keys (public and private keys) to authenticate users.
Port Forwarding
Dropbear also supports authentication agent forwarding for OpenSSH clients. It allows users to forward their SSH authentication agent connections, which enables the use of local private keys for authentication on remote servers without the need to copy those keys to the servers.
X11 Forwarding
Dropbear's server implements X11 forwarding, allowing users to run graphical applications on a remote server and display them locally. This feature manages applications on embedded systems or devices with limited resources.
Built-in SCP Server
Dropbear SSH inherently supports the Secure Copy Protocol (SCP), enabling straightforward file transfers between local and remote systems. This functionality is built into Dropbear, allowing users to copy files securely without additional configurations.
Comparison of Dropbear SSH with OpenSSH
| Feature | Dropbear SSH | OpenSSH |
|---|---|---|
| SSH (Protocol) | Lightweight SSH server and client for resource-constrained systems. | Open-source implementation of the SSH protocol, feature-rich and widely used. |
| Purpose | Designed for embedded systems, IoT, and minimal resource environments. | General-purpose SSH for secure remote login, file transfer, and tunneling. |
| License | Open-source, MIT-style license. | Open-source, BSD license. |
| Resource Usage | Extremely lightweight and suitable for devices with limited memory and CPU. | Moderate; Suited for servers, desktops, and high-resource environments. |
| Features | Core SSH functionality: encryption, authentication, port forwarding. | Comprehensive: encryption, tunneling, SFTP, key management, advanced configurations. |
| Platform Support | Embedded Linux, IoT devices, and resource-limited systems. | Cross-platform (Linux, Unix, macOS, Windows). |
| Ease of Installation | Easy to deploy on small systems due to minimal dependencies. | Comes pre-installed on most Unix-based systems. |
| Scalability | Suitable for small-scale or resource-constrained deployments. | Ideal for large-scale systems and complex environments. |
| Authentication Methods | Public key, password, host-based. | Public key, password, GSSAPI, host-based, keyboard-interactive. |
| File Transfer | Supports SCP (Secure Copy). | Supports SCP and SFTP (SSH File Transfer Protocol). |
| Security | Secure with encryption and authentication, but limited to core features. | Highly secure, frequently updated, and supports modern cryptographic algorithms. |
| Use Cases | IoT devices, routers, and embedded systems. | Servers, desktops, cloud platforms, enterprise networks. |
| Cost | Free and open-source. | Free and open-source. |
| Community Support | Smaller, niche community. | Large, active community with extensive documentation. |
The Architecture of Dropbear SSH
| Component | Description |
|---|---|
| Dropbear Server (dropbear) | The SSH server listens for incoming connections. |
| Dropbear Client (dbclient) | A lightweight SSH client that connects to remote servers. |
| Dropbear Key Management (dropbearkey) | A tool for generating and managing SSH keys. |
| Dropbear Conversion Tool (dropbearconvert) | Converts keys between OpenSSH and Dropbear formats. |
| Dropbear SCP (dropbearmulti) | Provides SCP file transfer functionality (without SFTP support). |
Core Components
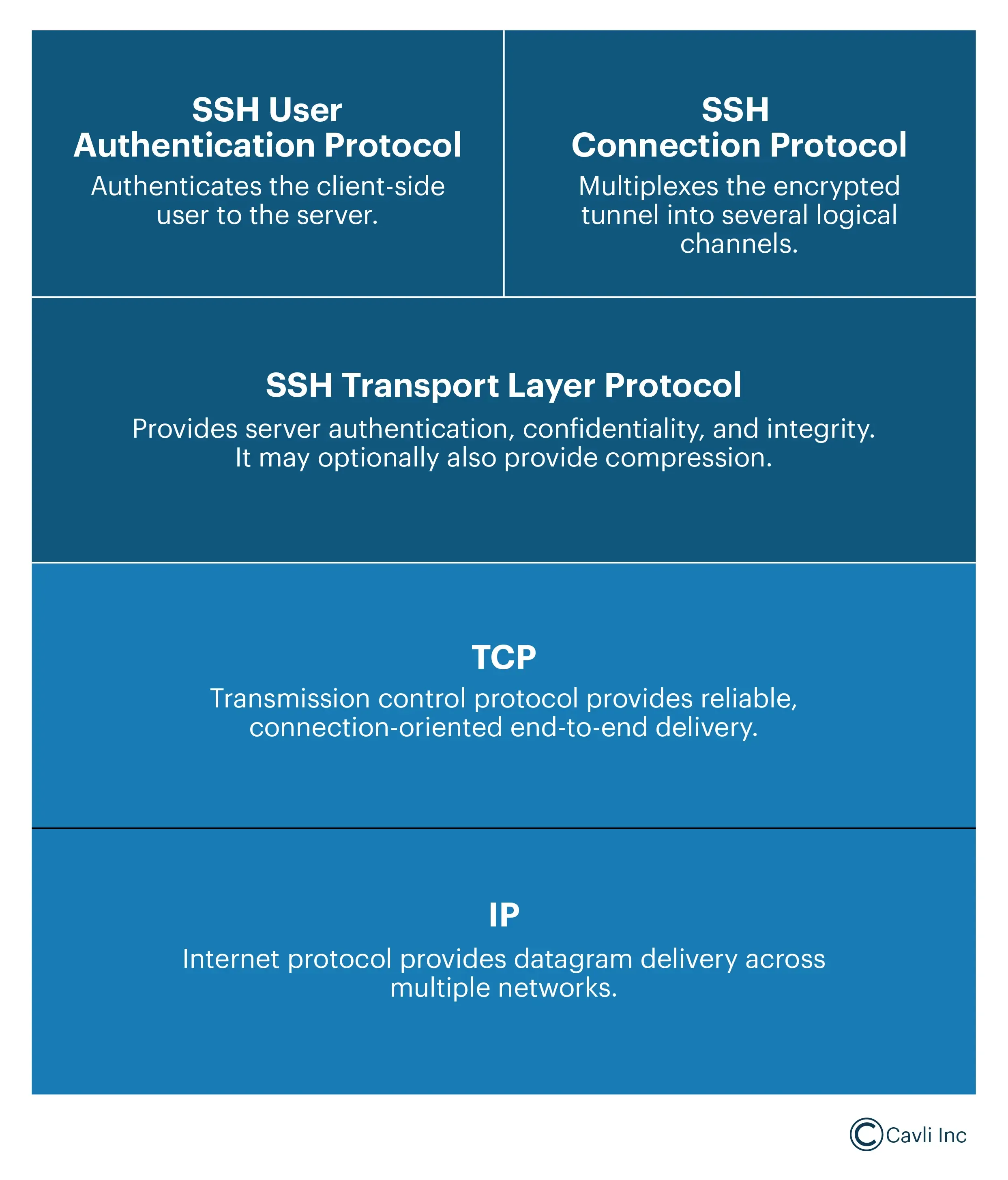
This represents a layered model of the SSH (Secure Shell) protocol stack in Dropbear, illustrating how different protocols work together to establish a secure remote communication session. Let's break down each layer:
IP (Internet Protocol) Layer (Bottom Layer)
- It provides basic packet delivery across multiple networks.
- It ensures that SSH packets can travel across the Internet or private networks.
- SSH uses IP addressing to identify the remote server.
TCP (Transmission Control Protocol) Layer
- It provides reliable, connection-oriented data delivery.
- SSH connections run over TCP (typically on port 22).
- TCP ensures error detection, retransmission, and in-order delivery of SSH packets.
- It guarantees that SSH messages are delivered correctly and completely.
SSH Transport Layer Protocol
- It provides fundamental SSH security, including encryption, integrity verification, and optional compression.
- This layer encrypts all communications using ciphers like AES, ChaCha20, and 3DES.
- It authenticates the server identity using public key cryptography (RSA, ECDSA).
- It protects against eavesdropping, man-in-the-middle attacks, and data tampering.
SSH User Authentication Protocol
- It authenticates the client (user) to the SSH server.
- It supports authentication methods such as:
- Public key authentication (default in Dropbear SSH).
- Password authentication (less secure, optional).
- It ensures that only authorized users can access the remote server.
SSH Connection Protocol (Top Layer)
- It manages multiple logical channels within a single SSH connection.
- It enables:
- Remote command execution (e.g., running shell commands).
- Port forwarding (Tunneling) (securely forwarding other network traffic via SSH).
- Secure file transfer (via SCP or SFTP when supported).
- Multiplexes (splits) SSH sessions so multiple activities (shell, file transfer, port forwarding) can simultaneously occur over a single SSH connection.
Encryption Mechanisms in Dropbear SSH
Dropbear SSH utilizes asymmetric and symmetric encryption techniques to secure communications between clients and servers.
Asymmetric Encryption (Public Key Cryptography)
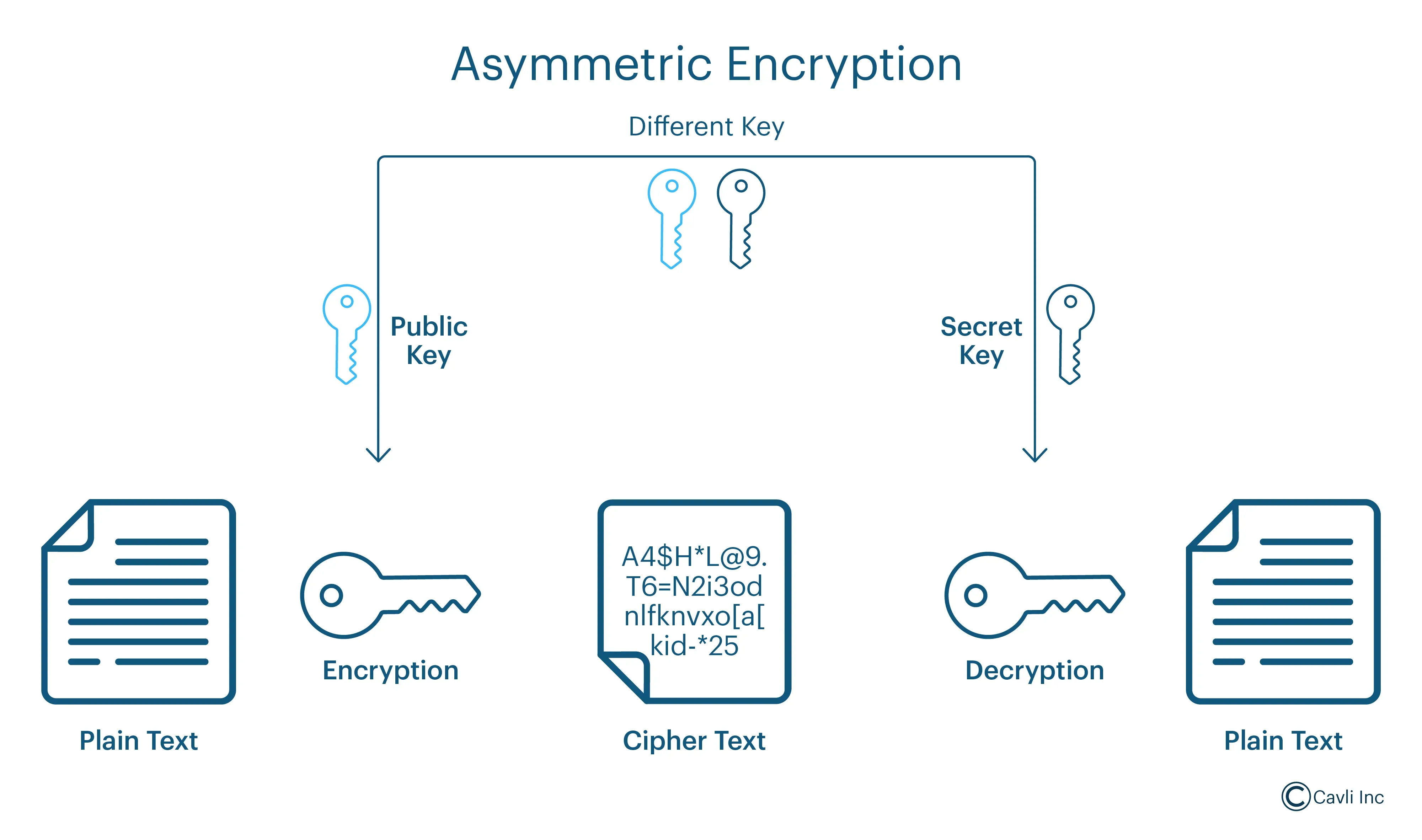
- It establishes a secure connection and authenticates parties without prior shared secrets.
- It utilizes a pair of cryptographic keys—a public and private key. The public key is openly shared, while the private key remains confidential. During the initial connection setup, asymmetric encryption facilitates the secure exchange of information, enabling both parties to verify each other's identities and establish trust.
Symmetric Encryption
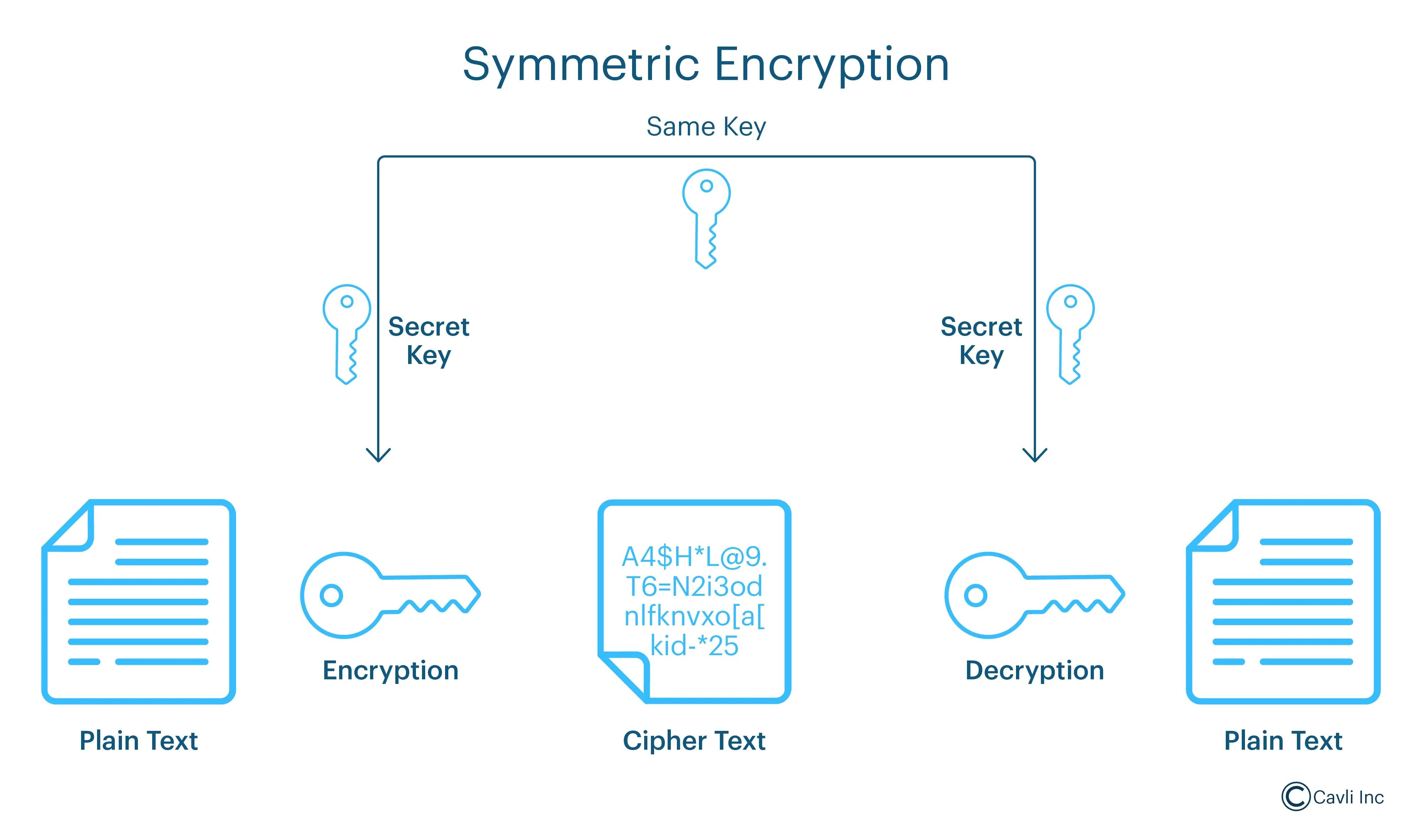
- It encrypts the data transmitted between the client and server during an active session, ensuring confidentiality and integrity.
- After establishing a secure connection using asymmetric encryption, Dropbear SSH employs symmetric encryption for the actual data transfer. Both parties use the same secret key, derived during the initial handshake, to encrypt and decrypt the data. This method is computationally efficient and suitable for encrypting large amounts of data in real time.
Integration in Dropbear SSH:
Dropbear SSH combines these encryption methods to provide a secure and efficient communication channel:
- Connection Initiation: The client initiates a connection to the Dropbear SSH server.
- Key Exchange and Authentication: Asymmetric encryption is employed to perform a key exchange and authenticate the server and, optionally, the client. This process establishes a shared secret between the two parties without transmitting it over the network.
- Data Transmission: With the shared secret established, symmetric encryption is used to encrypt the data transmitted between the client and server, ensuring confidentiality and integrity for the duration of the session.
By leveraging asymmetric and symmetric encryption techniques, Dropbear SSH ensures secure, authenticated, and confidential communication between clients and servers.
Commonly Used Code Snippets from Dropbear SSH Implementation
| Purpose | Code/Snippet | Description |
|---|---|---|
| Install Dropbear SSH | sudo apt-get install dropbear | Installs Dropbear on Debian-based systems. |
| sudo yum install dropbear | Installs Dropbear on Red Hat-based systems. | |
| Start Dropbear Server | dropbear | Starts the Dropbear SSH server with default settings. |
| dropbear -F -E | Starts Dropbear in the foreground with logging to stderr for debugging. | |
| Change Listening Port | dropbear -p 2222 | Configures Dropbear to listen on port 2222 instead of the default port 22. |
| Generate Host Keys | dropbearkey -t rsa -f /etc/dropbear/dropbear_rsa_host_key | Generates an RSA host key for the Dropbear server. |
| dropbearkey -t ed25519 -f /etc/dropbear/dropbear_ed25519_host_key | Generates an Ed25519 host key. | |
| Display Host Key Fingerprint | dropbearkey -y -f /etc/dropbear/dropbear_rsa_host_key | Displays the fingerprint of an existing RSA host key. |
| Run Dropbear with Custom Options | dropbear -p 2222 -w | Starts Dropbear on port 2222 and disables root login. |
| dropbear -p 2022 -g | Enables gateway ports for Dropbear on port 2022. | |
| Connect to a Server with Dropbear Client | dbclient user@hostname | Connects to a remote server using Dropbear’s client. |
| dbclient -i ~/.ssh/id_rsa user@hostname | Connects to a server using a specific private key. | |
| Secure File Transfer (SCP) | scp file.txt user@hostname:/destination/path | Transfers a file securely to a remote server using Dropbear’s SCP. |
| scp user@hostname:/source/file.txt /local/destination | Downloads a file securely from a remote server. | |
| Convert OpenSSH Key to Dropbear Format | dropbearconvert openssh dropbear openssh_key dropbear_key | Converts an OpenSSH private key to Dropbear’s format. |
| dropbearconvert dropbear openssh dropbear_key openssh_key | Converts a Dropbear private key to OpenSSH format. | |
| Stop Dropbear Server | pkill dropbear | Stops the Dropbear SSH server. |
| Check Running Dropbear Instances | ps aux | grep '[d]ropbear' | ps aux- This shows a snapshot of all running processes on the system. grep dropbear- This filters the output to show only lines that contain the word dropbear. |
| Restrict Root Login | dropbear -w | Starts Dropbear with root login disabled. |
| Log Access Attempts | dropbear -E | Logs all SSH access attempts to stderr for monitoring. |
| Enable Password Authentication | dropbear -s | Disables password authentication, allowing only public key authentication. |
| dropbear -A | Enables password authentication. |
Dropbear SSH and OpenWRT
Dropbear SSH and OpenWRT are closely related because Dropbear is the default SSH server in OpenWRT, the popular Linux-based firmware for embedded routers and networking devices.
OpenWRT (Open Wireless Router) is an open-source, Linux-based firmware primarily used for embedded devices like routers, access points, and network appliances. It replaces the stock firmware of consumer and enterprise networking hardware, providing greater flexibility, security, and advanced networking features.
How Dropbear Works in OpenWRT
Default SSH Server in OpenWRT
- Dropbear is pre-installed in OpenWRT firmware.
- It runs as a daemon (dropbear) to allow SSH access for remote management.
Secure Remote Management
- Allows users to securely configure OpenWRT devices remotely via SSH.
- Users can perform tasks like:
- Updating firewall rules.
- Managing network interfaces.
- Configuring VPNs.
File Transfer via SCP
- Since Dropbear does not support SFTP, OpenWRT users transfer files via SCP (Secure Copy Protocol).
Why Choose Dropbear SSH for IoT Applications?
Dropbear SSH has a significant connection with IoT (Internet of Things) applications due to its lightweight design, security capabilities, and compatibility with resource-constrained environments. IoT devices often operate with limited computational power, memory, and storage, making Dropbear SSH an ideal choice for secure communication and remote management.
Lightweight and Efficient Design
IoT devices such as sensors, gateways, and controllers typically have constrained hardware resources. Dropbear SSH minimizes system resource usage (memory, CPU, and storage), making it a suitable SSH solution for devices running on embedded Linux or similar environments.
Small Footprint for Mass Deployment
For large-scale IoT deployments involving hundreds or thousands of devices, Dropbear SSH’s small binary size (approximately 100KB) reduces storage requirements, enabling faster and cost-effective rollouts.
Port Forwarding for Communication
In IoT applications requiring secure data transmission across networks or firewalls, Dropbear SSH facilitates port forwarding, creating encrypted tunnels that ensure seamless communication between IoT devices and central servers.
Secure Remote Management
IoT devices require secure remote access for maintenance and debugging without physical intervention. Dropbear SSH provides encrypted channels for administrators to securely log in, troubleshoot issues, and configure devices remotely, ensuring uninterrupted operations.
Firmware Updates and File Transfers
Dropbear SSH supports SCP (Secure Copy Protocol) for transferring files securely, enabling IoT administrators to perform critical firmware updates and manage configuration files without compromising security.
Robust Security for IoT Networks
IoT devices are particularly vulnerable to cyberattacks. Dropbear SSH mitigates these risks with strong encryption (AES, 3DES, Twofish) and secure authentication methods such as public key, password-based, and host key verification. It ensures data integrity and protection against threats like eavesdropping and man-in-the-middle attacks.
IoT-Friendly Characteristics
- Resource Efficiency: Minimal RAM usage and low CPU overhead during encryption and decryption.
- Compatibility: Seamlessly integrates with embedded Linux systems, providing customizable compilation options for specific IoT requirements.
- Low Bandwidth: Optimized for devices with limited network resources, including battery-powered systems.
Use cases of Dropbear SSH in IoT
Smart Home Devices
In smart home devices, dropbear SSH enables secure, lightweight remote access and configuration for low-power home devices. It assists in remotely managing smart thermostats, security cameras, and lighting systems.
Industrial IoT (IIoT)
It securely monitors and controls PLCs (Programmable Logic Controllers) and SCADA systems in industrial IoT systems. It also provides secure remote diagnostics and updates for critical industrial machinery with minimal resource overhead.
Smart Cities
With Dropbear SSH, smart cities can manage environmental sensors, traffic monitoring systems, and public utility IoT devices. It allows secure communication and management of various distributed devices across city-wide networks.
Healthcare IoT
Dropbear SSH updates and monitors IoT-enabled medical devices, such as patient monitors and portable diagnostic equipment. It ensures compliance with data protection regulations through robust encryption while minimizing the impact on device performance.
Connected Vehicles
It helps manage telemetry and infotainment systems and other IoT-based diagnostics in vehicles. It facilitates secure updates and monitors automotive vehicle modules over constrained embedded systems.
Remote Environmental Monitoring
Dropbear SSH securely collects data from IoT-enabled weather stations or soil sensors in agriculture. It enables secure, remote data transfer and device updates in geographically dispersed locations.
Energy and Utilities
Dropbear SSH securely manages smart meters and IoT devices in power grids or water utilities. This ensures secure remote access to devices in resource-constrained environments while supporting scalability for large deployments.
Closing Notes
Dropbear SSH is a powerful and practical solution for secure remote access and management in resource-constrained environments, especially IoT applications. Its lightweight design, robust security features, and compatibility with embedded systems make it an indispensable tool for administrators managing distributed, low-power devices. By implementing best practices and adhering to strong security considerations, Dropbear SSH ensures encrypted communication, efficient device management, and protection against cyber threats. Whether streamlining IoT deployments, enabling secure firmware updates, or maintaining operational efficiency, Dropbear SSH remains a reliable choice for organizations looking to balance security, scalability, and performance in today’s interconnected world.
Go Beyond and Explore
What makes Dropbear SSH different from OpenSSH?
Is Dropbear SSH secure enough for production IoT deployments?
How much memory does Dropbear SSH typically require?
Can Dropbear SSH be used in battery-powered IoT devices?
What are the recommended security best practices for Dropbear SSH in IoT?
What is the default port of Dropbear SSH?
What is the SFTP protocol? When Should You Use FTP and SFTP?
FTP vs. SFTP
Use FTP when:
- Security is not a concern (e.g., transferring public files).
- Speed is the top priority in a trusted local network.
- The network environment already has FTP servers set up.
- Transferring sensitive data that needs encryption.
- Compliance and security (GDPR, HIPAA, etc.) are required.
- Working over untrusted networks (like the internet).



